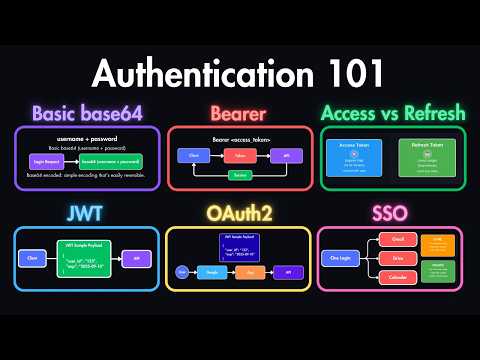
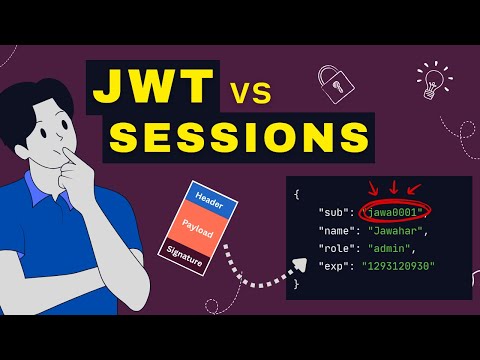
Are you doing authentication wrong? Many developers default to JWTs (JSON Web Tokens) for every project, but that is often a security mistake. In this video, we break down the evolution of authentication—from the "dinosaur" Basic Auth to Opaque Session Tokens and finally to JWTs—revealing exactly when you should use each one. We’ll cover why "stateless" isn't always better, the massive security risk of Basic Auth (base64 is NOT encryption!), and why the "Access + Refresh Token" pattern is the only way to safely use JWTs. 💡 KEY TOPICS IN THIS VIDEO: ✅ Why Basic Authentication is dangerous (Base64 vs Encryption) ✅ Stateful vs Stateless Authentication (Database hits vs CPU) ✅ How to implement secure login flows in Python/FastAPI ✅ The trade-offs of Opaque Tokens (Session IDs) ✅ Why you need Refresh Tokens to ban users instantly 📌 RESOURCES --------------------------------------------------- 🐙 GitHub Repo (Source Code): ⏱️ TIMESTAMPS --------------------------------------------------- 00:00 Introduction: Fixing your Authentication 00:21 Basic Authentication (The "Dinosaur" Setup) 00:50 Basic Auth Demo (FastAPI Example) 02:00 The Security Flaw of Basic Auth Headers 02:49 Opaque Tokens (The "Wristband" Approach) 03:13 Session Auth Demo & Revoking Access 04:08 Where to Store Tokens? (HTTPOnly Cookies vs LocalStorage) 04:53 JSON Web Tokens (JWT) Explained 05:22 The Access Token vs Refresh Token Pattern 05:42 JWT Demo: How Signatures & Payloads Work 07:15 Conclusion 👋 STAY CONNECTED --------------------------------------------------- 🎁 Join Our Discord: 📷 Instagram: 💼 LinkedIn: 🐦 X / Twitter: 🌐 Website: #Python #TelegramBot #Aiogram3 #PythonTutorial #Coding #Asyncio
- 118Просмотров
- 1 неделя назадОпубликованоAlmaz | Automation
YOUR AUTH IS BROKEN: JWT vs Sessions vs Basic Auth Explained
Похожее видео
Популярное
Hercules nemean lion
Красная гадюка часть ,6
oso
потерянный снайпер
Красная гадюка4
потерянній снайпер
2 сезон городской снайпер
Красная гадюка 4
барбоскины выпуск 8 диск
Потеринний снайпер.3серия
Фильм потеряны снайпер
klaskyklaskyklaskyklasky gummy bear g major 26
Он іздевался над женой
ВЕЛОСПОРТ ЮРИЙ ПЕТРОВ .
обнаженная
Красуня гадюка3
Божественний доктор
Гоу дигео
Щенячий патруль
настольная игра реклама
Universal 2003 hd
Сутінки розділ 3
ШАРЛОТТА ЗЕМЛЯНИКА
women bathe boys
Красная гадюка часть ,6
oso
потерянный снайпер
Красная гадюка4
потерянній снайпер
2 сезон городской снайпер
Красная гадюка 4
барбоскины выпуск 8 диск
Потеринний снайпер.3серия
Фильм потеряны снайпер
klaskyklaskyklaskyklasky gummy bear g major 26
Он іздевался над женой
ВЕЛОСПОРТ ЮРИЙ ПЕТРОВ .
обнаженная
Красуня гадюка3
Божественний доктор
Гоу дигео
Щенячий патруль
настольная игра реклама
Universal 2003 hd
Сутінки розділ 3
ШАРЛОТТА ЗЕМЛЯНИКА
women bathe boys
Новини