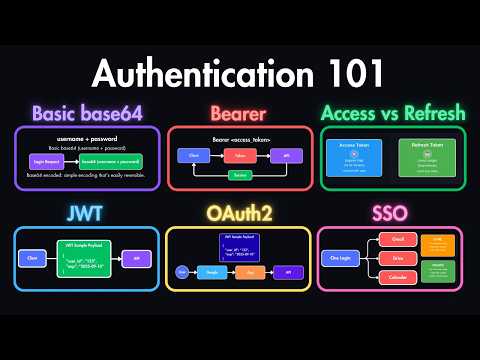
If you're building a mobile app, single-page app (SPA), or browser-based tool that uses OAuth — PKCE is essential. PKCE (Proof Key for Code Exchange) is a powerful security upgrade to the OAuth 2.0 Authorization Code Flow. It protects users from authorization code interception attacks — especially when your app can't safely store a client secret. In this video, we break down: - Why traditional OAuth isn't safe for public clients - What PKCE is and how it solves the code interception problem - The step-by-step PKCE flow using real-world examples - Code samples and architecture walkthroughs - How tools like VS Code, Spotify, and Auth0 use PKCE today You’ll leave with a crystal-clear understanding of how PKCE works, where to use it, and why it’s now the default for secure OAuth flows in SPAs and mobile apps. 🔐 Watch this before building your next login system! ⏱️ Timestamps 0:00 – Intro: Why OAuth Needs PKCE for Public Clients 0:42 – Quick OAuth 2.0 Recap & What’s Broken 1:28 – What is PKCE? (Proof Key for Code Exchange) 4:29 – The Problem PKCE Solves (Code Interception) 4:52 – How the PKCE Flow Works (Step-by-Step) 5:52 – JavaScript Code Example of PKCE in Action 6:56 – Real-World Use Cases: Mobile, SPA, CLI 7:40 – Gmail Case Study: When PKCE is Optional 8:40 – The Future: OAuth 2.1, CAEP & Beyond AWS Certification: AWS Certified Cloud Practioner: AWS Certified Solution Architect Associate: AWS Certified Solution Architect Professional: #PKCE #OAuth2 #WebSecurity #MobileSecurity #Bytemonk
- 13733Просмотров
- 4 месяца назадОпубликованоByteMonk
OAuth is Broken Without This | Meet PKCE
Похожее видео
Популярное
ну погоди 17-18 выпуск
Красна я гадюка 6
веселая-карусел-14
Красная гадюка 14-20 серии
Kion lion king trailer 2026
ВОЛШЕБНАЯ КАРУСЕЛЬ
Лихач 3 сезон 1-4
потерянный снайпер 6 серия
Смешарики титры
Стражи правосудия 3 сезон
formation
ну погоди 1-16 выпуски
poterianij snaiper 2 seria
комедия
Wb 2018 effects nice
Потерянный снайпер 4 серия
girls feet
https:/www.google.com/url
Beast rogue lion
Стражи правосудия
humiliation
беззаконник 3
красный тарантул часть 3
Law and order criminal intent season 5 intro
Сутінки розділ 3
Красна я гадюка 6
веселая-карусел-14
Красная гадюка 14-20 серии
Kion lion king trailer 2026
ВОЛШЕБНАЯ КАРУСЕЛЬ
Лихач 3 сезон 1-4
потерянный снайпер 6 серия
Смешарики титры
Стражи правосудия 3 сезон
formation
ну погоди 1-16 выпуски
poterianij snaiper 2 seria
комедия
Wb 2018 effects nice
Потерянный снайпер 4 серия
girls feet
https:/www.google.com/url
Beast rogue lion
Стражи правосудия
humiliation
беззаконник 3
красный тарантул часть 3
Law and order criminal intent season 5 intro
Сутінки розділ 3
Новини