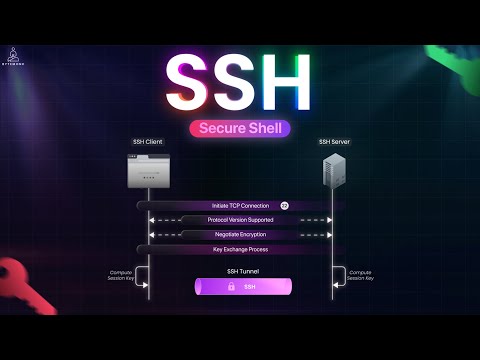
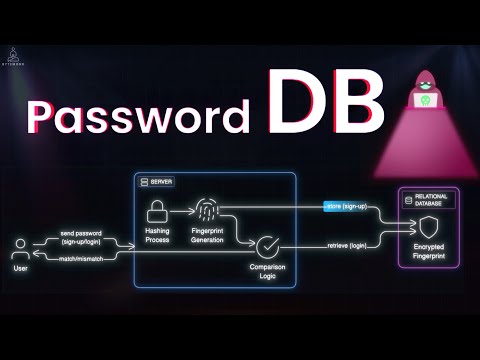
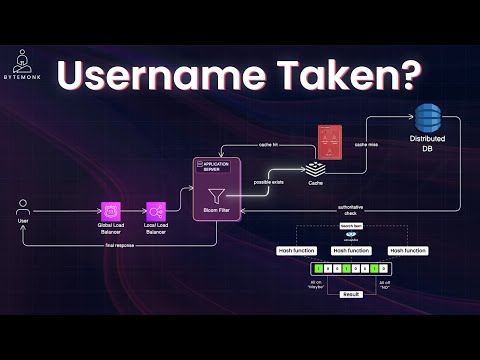
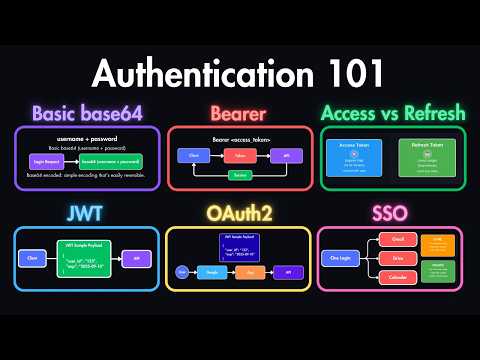
Identity and Access Management (IAM) is the invisible engine behind every secure login — from GitHub to Google Workspace to AWS. But how does it all really work? In this video, we break IAM down into clear, digestible parts: - What is IAM? (Identity + Access Control) - How Identity Providers (IdPs) authenticate users - How Federation enables Single Sign-On (SSO) - The difference between AuthN and AuthZ - Why protocols like OAuth, SAML, and SCIM matter - How companies use AWS IAM + Okta + custom flows - Real-world architecture diagrams and role-based access in action Whether you're building apps or auditing systems, this video will give you a solid grasp of how IAM works — from login to permissions. 🔐 Don’t forget to explore the full System Design & Security playlist on this channel! ⏱️ Timestamps 0:00 – Intro: What IAM Solves 0:40 – What is IAM? Identity + Access Explained 1:30 – How Identity Providers (IdP) Work 2:20 – Real Login Example: “Sign in with Google” 3:10 – Federation & SSO: Single Sign-On Basics 4:10 – Authentication vs Authorization (AuthN vs AuthZ) 5:00 – RBAC, ABAC, and Access Models 6:00 – AWS IAM: Roles, Policies, and Federation 7:00 – Custom IAM Systems in Regulated Industries 7:40 – SCIM & Provisioning: How Users Get Synced 8:30 – End-to-End IAM Architecture Flow #iam #IdentityAccessManagement #SSO #OAuth #SAML #SCIM #Authentication #Authorization #AWSIAM #Bytemonk #SecurityArchitecture
- 15310Просмотров
- 4 месяца назадОпубликованоByteMonk
What Happens When You Login? | IAM Secrets Used by Big Tech
Похожее видео
Популярное
Angela White
Фул школьниц
потерянній снайпер 2
Pushpa 2 rashmika mandanna
Universal 2013 in zoopals
Wb effects
Потеряный снайпер 3 серия
Anny_6Feet10
reupload my edited video bb into song version
ббурное безрассудство 2
сакс игрушки
Красная гадюка 17
оазис
Robinhood sreeleela speech
Сериал я жив
бен 10
малыш вилли 03
Jingle bells kids song
СКАЗКИ ЛЮПИНА
Шрек
женитьба бальзаминова
красный тигр
Поточний снайпер 2
все серии жина чиновника
Фул школьниц
потерянній снайпер 2
Pushpa 2 rashmika mandanna
Universal 2013 in zoopals
Wb effects
Потеряный снайпер 3 серия
Anny_6Feet10
reupload my edited video bb into song version
ббурное безрассудство 2
сакс игрушки
Красная гадюка 17
оазис
Robinhood sreeleela speech
Сериал я жив
бен 10
малыш вилли 03
Jingle bells kids song
СКАЗКИ ЛЮПИНА
Шрек
женитьба бальзаминова
красный тигр
Поточний снайпер 2
все серии жина чиновника
Новини