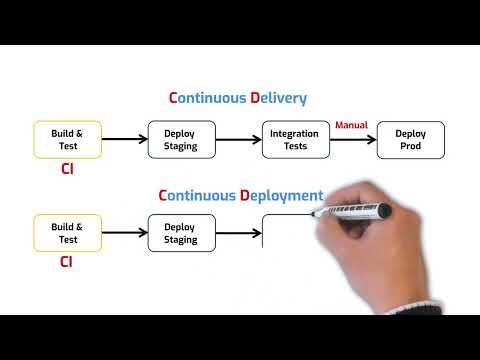
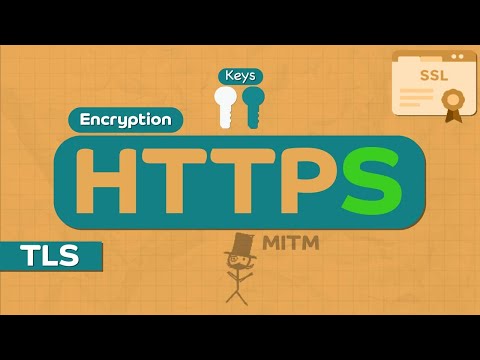
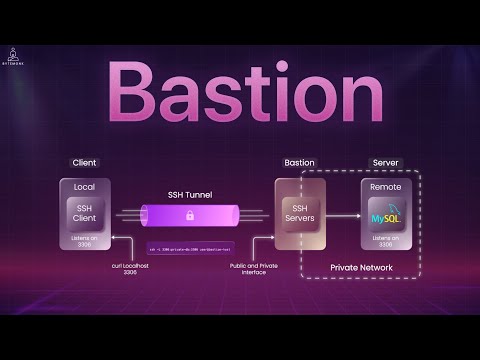
SSH (Secure Shell) is the gold standard for securely accessing and managing remote servers. In this video, we’ll break down how SSH works under the hood, why it replaced Telnet, and how developers and DevOps teams use it every day. 💡 **What you'll learn:** - How SSH establishes a secure, encrypted connection - SSH vs. Telnet — the postcard vs. locked briefcase analogy - Key-based authentication vs. passwords - Real-world examples: AWS EC2 `.pem` files & GitHub SSH keys - SSH port forwarding (tunneling) for databases & private tools Whether you’re deploying code, managing servers, or setting up secure automation, this guide will make SSH clear and approachable. ⏱️ Timestamps 00:00 Intro — Why SSH Matters 00:42 What is SSH & Why Use It? 01:35 SSH vs Telnet (Secure vs Insecure Shell) 02:26 How SSH Works — Encryption & Key Exchange 04:15 Authenticating with SSH — Keys vs Passwords 05:18 Real-World Example: AWS EC2 .pem File 06:05 Real-World Example: GitHub SSH Keys 06:42 SSH Local Port Forwarding (Tunneling) AWS Certification: AWS Certified Cloud Practioner: AWS Certified Solution Architect Associate: AWS Certified Solution Architect Professional: #SSH #SecureShell #SystemDesign #Cybersecurity #RemoteAccess #Encryption #Authentication #PortForwarding #Telnet
- 25396Просмотров
- 4 месяца назадОпубликованоByteMonk
How SSH Works | Keys, Encryption & Real-World Examples
Похожее видео
Популярное
Красная гадюка 4серия
опасность
سكس
Universal not scary
لخت
комедия
БУРНОЕ БЕЗРАССУДСТВО 3
красная гадюка сезон 2
красный тарантул
Потераний снайпер 2
Pororo russian
Обриси
взлом карусели
маленькая девочка
улица далматинцев 101
Фул школьниц
przepraszamy za usterki
Стражи правосуддя 5
Лупдиду
Красная гадюка 5 серия
Сутінки розділ 3
lenny barn 2
Заставки Тижи TiJi
2х2 лёлик и барбарики
опасность
سكس
Universal not scary
لخت
комедия
БУРНОЕ БЕЗРАССУДСТВО 3
красная гадюка сезон 2
красный тарантул
Потераний снайпер 2
Pororo russian
Обриси
взлом карусели
маленькая девочка
улица далматинцев 101
Фул школьниц
przepraszamy za usterki
Стражи правосуддя 5
Лупдиду
Красная гадюка 5 серия
Сутінки розділ 3
lenny barn 2
Заставки Тижи TiJi
2х2 лёлик и барбарики
Новини