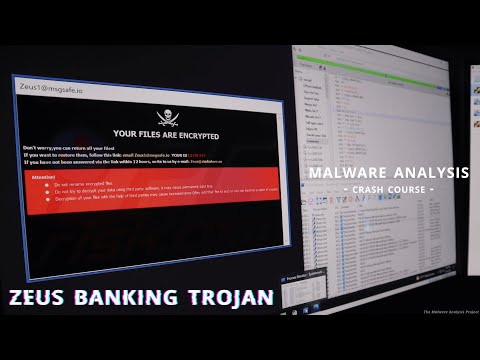
In this in-depth malware analysis video, we dissect the Emotet malware (disguised as a payroll invoice) using Ubuntu, Flare VM, and REMnux for both static and dynamic network traffic simulation. 🔍 What you'll learn: Using Oletools ( & ) to identify malicious VBA macros and extract obfuscated Base64 payloads. Leveraging Didier Stevens Suite (oledump) for deeper inspection of data streams and malicious entries. Conducting dynamic analysis on Flare VM with Process Monitor & Wireshark to observe execution and identify C2 communication URLs. Capturing and analyzing network traffic on REMnux to simulate real-world Emotet callbacks. 💡 Tools covered: Oletools ( , ) Didier Stevens Suite (oledump) Process Monitor & Wireshark Flare VM & REMnux This video is ideal for malware analysts, incident responders, threat hunters, and cybersecurity students who want to understand the behavior and indicators of compromise (IOCs) of Emotet variants.
- 114Просмотров
- 4 месяца назадОпубликованоKiso Secure
Emotet Malware Analysis: De-obfuscating Malicious VBA Macros & Payloads
Похожее видео
Популярное
чиполлино
взлом карусели
Красная гадюка 2
дисней добрлас
Потерений снайпер 2
Spongebob
Секс и дзен 1
Красная гадюка 4серия
mickey mouse clubhouse
Красная гадюка 5часть
klaskyklaskyklaskyklasky joey 2 do go
Robinhood sreeleela
Безжалостный гений 3
masculine men
МОЛАНГ
Valu stupid wife temporada finale series
Youtube
ну погоди 18 выпуск
паляниця
Pororo
efootball
потерянный снайпер 5
Красный тарантул 8 серия
хулиган и пай девочка
взлом карусели
Красная гадюка 2
дисней добрлас
Потерений снайпер 2
Spongebob
Секс и дзен 1
Красная гадюка 4серия
mickey mouse clubhouse
Красная гадюка 5часть
klaskyklaskyklaskyklasky joey 2 do go
Robinhood sreeleela
Безжалостный гений 3
masculine men
МОЛАНГ
Valu stupid wife temporada finale series
Youtube
ну погоди 18 выпуск
паляниця
Pororo
efootball
потерянный снайпер 5
Красный тарантул 8 серия
хулиган и пай девочка
Новини