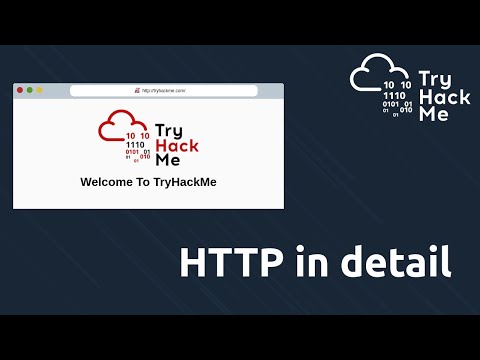
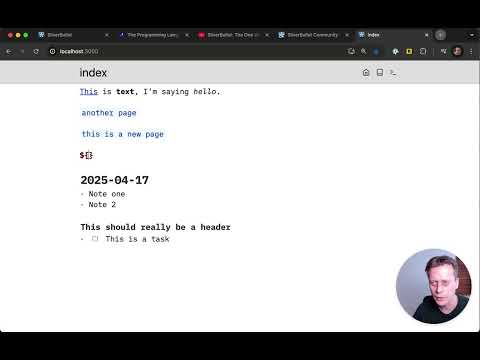
Overview and demonstration of how to use Netexec with the SMB protocol against Active Directory hosts within a home lab environment. ▬ Contents of this video ▬▬▬▬▬▬▬▬▬▬ 00:00 Intro 00:55 Netexec Configuration File 04:53 Targets - Subnet 05:30 Targets - Generate Hosts File 06:31 Targets - FQDN 06:55 Targets - Text File 08:20 Authentication - Domain Username/Password 10:44 Authentication - Pass-The-Hash 11:12 Authentication - Kerberos 12:30 Authentication - Certificates 14:02 Netexec Database 14:45 Netexec Database - Creds 15:37 Authentication - Creds Database ID 17:45 Authentication - Local User Username/Password 19:09 Password Policy Enumeration 20:23 Password Spraying 23:07 Password Attack - Wordlist 24:34 Password Attack - No Brute Force 26:40 SAM Database Dump 27:12 LSA Secrets Dump 27:55 NTDS Dump 29:13 Shares Enumeration 30:33 Spidering Shares 33:18 Interface Enumeration 34:42 Logged On Users 36:03 User Session Enumeration 36:40 Users Enumeration 37:13 Local Group Enumeration 38:08 Tasklist Enumeration 38:30 Executing Commands Remotely 38:57 Transfer and Execute Reverse Shell 40:33 SMB Modules 41:05 SMB Modules - Add Computer 43:20 SMB Modules - Spider Plus 46:30 SMB Modules - LSASSY 48:52 SMB Modules - Impersonate 51:10 Conclusion Netexec Wiki:
- 81Просмотров
- 6 дней назадОпубликованоr1ckyr3c0n
Using Netexec SMB Protocol
Похожее видео
Популярное
ПОТЕРЯННЫЙ СНАЙПЕР2
ну погоди 18 выпуск
Безжалостный гений 3
барбоскины выпуск 8 диск
МИСТЕР МЭН
Стрекоза и муравей
Mesis purple
poterianij snaiper 2 seria
grasshopper code
Лихач 2025
Грань правосудия 4 сезон
сильвания фэмили реклама
tushy
Фул школьниц
сорванцы
Noddy - Episo’dio 21 (A dia de folga da Dina)
Городскои снаипер 8
Фильм потеряны снайпер
Universal picturesworkingtitie nanny McPhee
Universal gmajor
baywatch
детский сад
потерянный снайпер 2
ну погоди 18 выпуск
Безжалостный гений 3
барбоскины выпуск 8 диск
МИСТЕР МЭН
Стрекоза и муравей
Mesis purple
poterianij snaiper 2 seria
grasshopper code
Лихач 2025
Грань правосудия 4 сезон
сильвания фэмили реклама
tushy
Фул школьниц
сорванцы
Noddy - Episo’dio 21 (A dia de folga da Dina)
Городскои снаипер 8
Фильм потеряны снайпер
Universal picturesworkingtitie nanny McPhee
Universal gmajor
baywatch
детский сад
потерянный снайпер 2
Новини