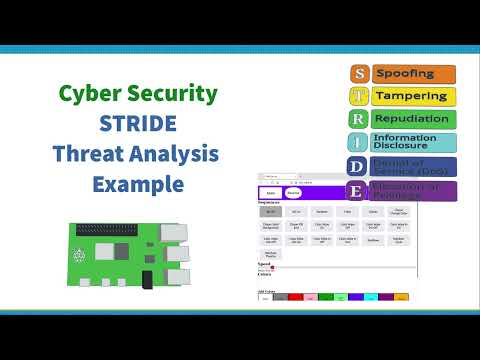
This video provide an introduction to the theory behind threat modelling and analysis using the STRIDE categorization scheme. It provides a way to identify threats to software you are developing yourself as well as off-the-shelf software products. This is one of the things you need to know if you are planning to gain CISSP cybersecurity certification. The video talks about the theory on creating a data flow diagram, and how the analysis is then applied. In a future video I plan to create another video with a practical example of how to apply STRIDE analysis to an open source software projects. The 6 steps to STRIDE are: Spoofing Tampering Repudiation Information Disclosure Denial of Service DoS Elevation of privilege For more details see: Chapters: 00:00 Threat modelling / analysis 00:15 Why threat modelling 01:15 Threat modelling and software lifecycle 02:05 Identifying threats 02:50 Stride mnemonic 06:21 Data Flow Diagram 06:42 Microsoft Threat Analysis tool 07:08 Summary
- 12350Просмотров
- 3 года назадОпубликованоPenguin Fortress - Cybersecurity Information
Security Threat Modelling / Analysis - using STRIDE - useful for CISSP certification #cybersecurity
Похожее видео
Популярное
Акулв
Красна я гадюка 4
Красна я гадюка 6
Красная гадюка 16 серия
малыш вилли
Бобр добр
Свинка пеппа
Потерянный снайпер часть 6
Божественний доктор
Classic caliou misbehaves on a road
веселая-карусел-11
Смешарики
bungalow colony
тарзан фильм
Красная гадюка 13 серия
Сутінки 2
дисней добрлас игрушки
car brands a z
Are you sure universal 2010
Божественний доктор
Тверская 2 сезон
Bing gets grounded
Потерянный снайпер часть 2
Красная гадюка 14 серия
Rayton M01
Красна я гадюка 4
Красна я гадюка 6
Красная гадюка 16 серия
малыш вилли
Бобр добр
Свинка пеппа
Потерянный снайпер часть 6
Божественний доктор
Classic caliou misbehaves on a road
веселая-карусел-11
Смешарики
bungalow colony
тарзан фильм
Красная гадюка 13 серия
Сутінки 2
дисней добрлас игрушки
car brands a z
Are you sure universal 2010
Божественний доктор
Тверская 2 сезон
Bing gets grounded
Потерянный снайпер часть 2
Красная гадюка 14 серия
Rayton M01
Новини