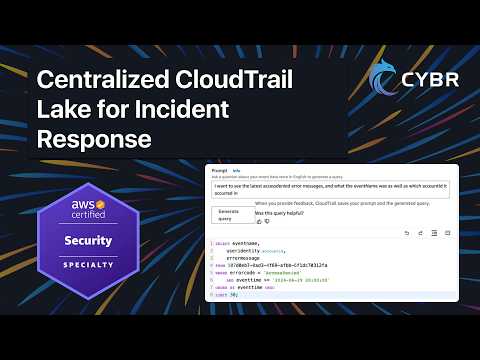
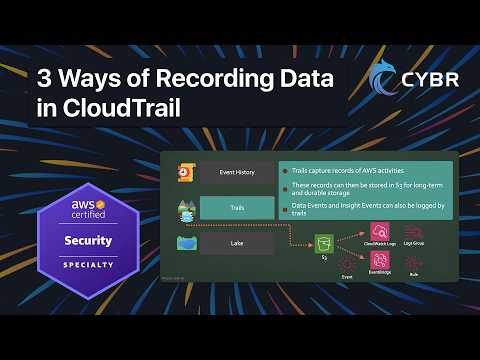
Copy/paste the bucket policies from here (just requires a free account): Need help configuring AWS CloudTrail and Incident Response workflows for your organization? Contact us for expert, hands-on help, at In this lesson from our AWS Certified Security Specialty (SCS-C03) course, we walk through how to deploy an organization-wide CloudTrail trail using a proper multi-account security architecture. Instead of configuring CloudTrail in a single account, we centralize logging across all accounts in an AWS Organization and send logs to a dedicated Log Archive account, while managing CloudTrail from a separate Security Tooling account, aligned with the AWS Security Reference Architecture. You’ll learn: • The difference between single-account and organization-wide CloudTrail deployments • How to delegate CloudTrail administration • How to configure the required S3 bucket policy in the Log Archive account • How to create and enable an organization trail • What changes when you enable “All accounts in my organization” • How to verify logs are being delivered properly • Why multi-Region logging matters for security We also discuss production considerations such as SSE-KMS encryption, log file validation, versioning, Object Lock, lifecycle rules, and why this should ideally be deployed with Infrastructure as Code or AWS Control Tower. By the end of this lesson, you’ll have: • Centralized logging across all accounts • Separation of duties between Security Tooling and Log Archive • Immutable log storage for security investigations This is a foundational architecture pattern you’re expected to understand for the exam and for real-world cloud security environments. #AWS #AWSCertified #AWSSecuritySpecialty
- 42Просмотров
- 5 дней назадОпубликованоCybr
Deploying AWS CloudTrail Organization Trail - SCS-C03
Похожее видео
Популярное
Дельфин 4
Красная гадюка
Фивел
Walt Disney pictures 2011 in g major effects
Tschu tschu wa
Красная гадюка 6
Бурное безрассудно 2 часть
скорей скорей
Потеряный снайпер
сериал
фиксики
Волшебная карусель
красный тигр-1
Valu stupid wife christmas special
girls feet
Красная гадюка 13серия
Стражи правосудия 5
Красная гадюка часть 3
ШАРЛОТТА ЗЕМЛЯНИКА
Смешарики
БУРНОЕ БЕЗРАССУДСТВО 3
Обризи
Дельфин
Баскервиллей
Красная гадюка
Фивел
Walt Disney pictures 2011 in g major effects
Tschu tschu wa
Красная гадюка 6
Бурное безрассудно 2 часть
скорей скорей
Потеряный снайпер
сериал
фиксики
Волшебная карусель
красный тигр-1
Valu stupid wife christmas special
girls feet
Красная гадюка 13серия
Стражи правосудия 5
Красная гадюка часть 3
ШАРЛОТТА ЗЕМЛЯНИКА
Смешарики
БУРНОЕ БЕЗРАССУДСТВО 3
Обризи
Дельфин
Баскервиллей
Новини