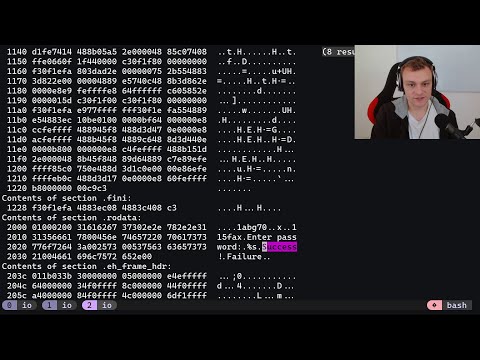
Even Sudo can get hacked once in a while. I walk through CVE-2025-32463, a critical privilege escalation vulnerability affecting certain versions of the "sudo" command in Linux. I show a publicly available Proof-of-Concept running out of the box. Then I show how you can modify it to get it to work in different scenarios. Chapters: 0:00 Intro 0:45 Available Write Ups 1:08 CVE Key Points 2:17 Exploit Demo 3:00 Set Up Lab Environment 4:25 Does a Vulnerable Version Equal Exploitable? 5:47 Set Up Lab Environment Cont.. 6:40 Running Exploit Out-of-Box 7:25 Setting Up Exploit w/ Limited Software on Target 9:45 Modifying PoC Bash Script 11:20 Transfer Files to Target 11:50 Running Modified Exploit Script #cybersecurity #linux #ethicalhacking //Disclaimer // Hacking without permission is illegal. This is strictly educational, and for learning about ethical hacking/ penetration testing in the cybersecurity space so that we can better protect ourselves against the bad guys.
- 916Просмотров
- 5 месяцев назадОпубликованоByteStryke
Exploiting Sudo CVE-2025-32463: From User with Chroot to Root
Похожее видео
Популярное
2х2 лёлик и барбарики
барбоскины выпуск 8 диск
Потерянный снапер 2
mia malkova hot tub
машенька
Fap teen
винни пух все серии
Tai tai
Потерений снайпер 2
car brands a z
https:/www.totosi.it/casino
барбарики барбарелла
щенячий патруль реклама
Городскои снаипер 8
Красная гадюка часть ,6
потеряій снайпер 5 серия
Вулиця сезам
after 14 Years
красный тарантул часть 3
ПОТЕРЯННЫЙ СНАЙПЕР 3
oso
feet city
Картоплини та дракони
formation
Фильм Красная гвоздика 2
барбоскины выпуск 8 диск
Потерянный снапер 2
mia malkova hot tub
машенька
Fap teen
винни пух все серии
Tai tai
Потерений снайпер 2
car brands a z
https:/www.totosi.it/casino
барбарики барбарелла
щенячий патруль реклама
Городскои снаипер 8
Красная гадюка часть ,6
потеряій снайпер 5 серия
Вулиця сезам
after 14 Years
красный тарантул часть 3
ПОТЕРЯННЫЙ СНАЙПЕР 3
oso
feet city
Картоплини та дракони
formation
Фильм Красная гвоздика 2
Новини