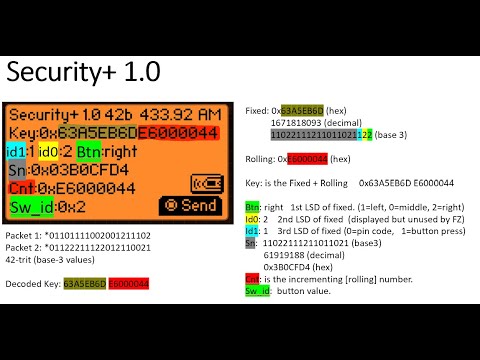
This video is for Educational Purposes************************ Please review video for resource references. IoT Devices are vulnerable because most devices use . can travel further. So, it is still in use today. Flipper Notes: Scan - AP List - AP Select - AP Save to flipper sdcard - yes - yes Sniff - pmkid - Targeted Active (Force Deauth) (Let run for about 5 minutes) WireShark: Open wireshark and Search for EAPOL. Then save the file to be converted. See below. Hashcat: Used to convert the PCAP file Hashcat for cracking hashed passwords Dictionary Attack Combination Attack Mask Attack Note: When performing command line tasks make sure your referencing everything in the correct directory. Github: Look up Danielmiessler SecLists on google and you should find the wordlist on github. Shout out to danielmiessler! Cmd Ran: -m 22000 Note: To help protect yourself from this type of an attack use an extremely long and complex password.
- 44757Просмотров
- 1 год назадОпубликованоCuevista
Flipper Zero - Unleashed - Marauder Deauth Hacking Cracking Wifi Passwords for Educational Purposes
Похожее видео
Популярное
ШАРЛОТТА ЗЕМЛЯНИКА
ultramen
Menu dvd Lex olivie remake
Потерянный снайпер часть 2
паляниця
Безжалостный гений 3
Stevie Emerson
потерянный снайпер
Фивел
томас и его друзья елка
красный тарантул 3сезон
ПОТЕРЯННЫЙ СНАЙПЕР 3
гача лайф
Youtube
mickey Valentine day party part 2
Грань правосудия фильм 4
Menu dvd Lex olivie remake monstros sa
ЖИЗНЬ ПЕТРОВИЧА В США
Лихач 4 сезон 7-9
Красный тарантул 3 часть
Universal g major 7
Финал
веселая-карусел-10
Universal gmajor
ultramen
Menu dvd Lex olivie remake
Потерянный снайпер часть 2
паляниця
Безжалостный гений 3
Stevie Emerson
потерянный снайпер
Фивел
томас и его друзья елка
красный тарантул 3сезон
ПОТЕРЯННЫЙ СНАЙПЕР 3
гача лайф
Youtube
mickey Valentine day party part 2
Грань правосудия фильм 4
Menu dvd Lex olivie remake monstros sa
ЖИЗНЬ ПЕТРОВИЧА В США
Лихач 4 сезон 7-9
Красный тарантул 3 часть
Universal g major 7
Финал
веселая-карусел-10
Universal gmajor
Новини