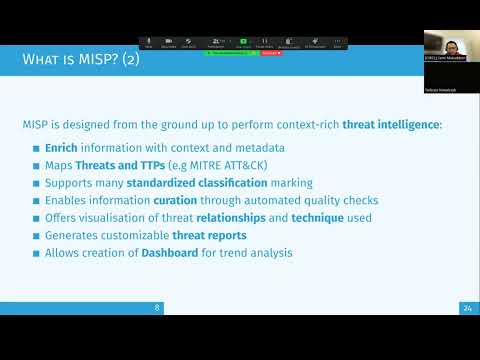
What is MISP threat intelligence sharing platform, and how can you play with the threat intelligence feeds? This short demo shows you how to access the default data feeds provided by the CIRCL virtual machine. While MISP's greatest strength is to automate your network defences to block and filter known threats, it is also an incredibly useful database for threat research and incident response analysis. In future videos, I will show you how to use other features, but this is a brief introduction. 4:18 Start of the demo Links in video: Link to VM: ---- HEFESTIS: ---- Follow Me Online Here: LinkedIn: Jordan's site: ---- Check out my Cyber Security books: "Advanced Persistent Training" "Cask Strength Security Non-Compliance: Four Ways to Respond When Someone Breaches Cybersecurity Policy" ---- CPE entry (CSV): Link, Type, Title, Presenter, Year Published, Domain, Length , video/webinar, Intro to MISP, Jordan M Schroeder, 2020, Security Operations, 9:00
- 58207Просмотров
- 5 лет назадОпубликованоJordan M. Schroeder
Intro to MISP | Demo of the MISP virtual machine
Похожее видео
Популярное
алиса в стране чудеса
Universal 1997 2012 g. Major 4
Universal not scary in Luigi group
Грань правосудия 5
Красная годюка 5 часть
топлес
ending 4134
navy boat crew
CPXV02 14
Профиссионал
Видео потеряный снайпер
Смывайся
hentai
timon pumbaa
ПЕРСИ И ЕГО ДРУЗЬЯ
Финал
forsaken fandom
Preview Disney 2011 effects
городской снайпер 8 серия
ну погоди 18 выпуск
Красная гадюка 11 серия
Universal low voice effects 2013
обнаженная
Universal 1997 2012 g. Major 4
Universal not scary in Luigi group
Грань правосудия 5
Красная годюка 5 часть
топлес
ending 4134
navy boat crew
CPXV02 14
Профиссионал
Видео потеряный снайпер
Смывайся
hentai
timon pumbaa
ПЕРСИ И ЕГО ДРУЗЬЯ
Финал
forsaken fandom
Preview Disney 2011 effects
городской снайпер 8 серия
ну погоди 18 выпуск
Красная гадюка 11 серия
Universal low voice effects 2013
обнаженная
Новини