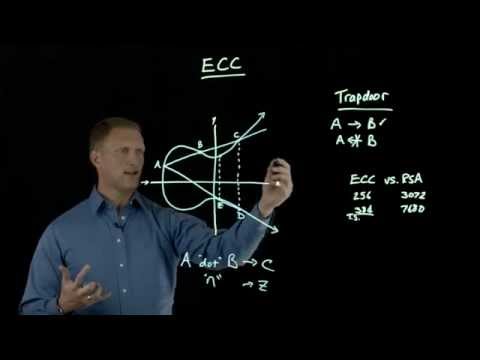
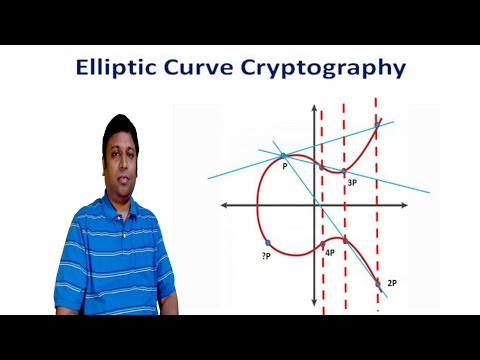
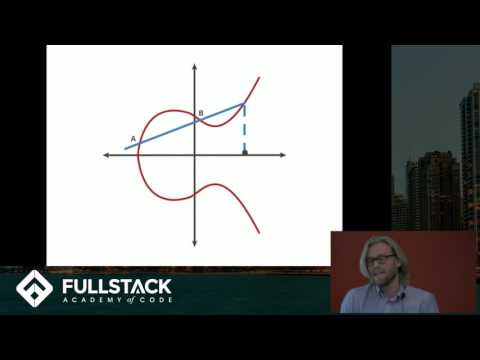
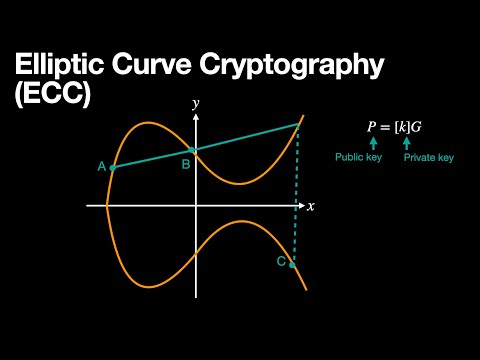
ECC, or Elliptic Curve Cryptography, is the most secure and modern way of doing Cryptography. But what is it really? What are the most important parts of understanding ECC? In this video, we give you the framework for seeing that ECC is really not all that different from the Cryptography you might already be familiar with. // CHAPTERS 0:00 - Intro 0:25 - Review of Asymmetric Cryptography 1:03 - What is an Elliptic Curve? 1:45 - Points on a Curve as values in Math formulas 2:09 - RSA, DSA, and DH 3:02 - ECRSA, ECDSA, and ECDH 3:27 - ECC is more secure, and require smaller keys 3:58 - Outro / Summary // FULL SERIES - Cryptography Essentials // This video is part of a 16-part series covering the essentials of modern Cryptography. Explained simply, and technically accurate. The full series is available here: 📋 ( or use the shortcut ) 00 Series Introduction 01 Hashing 02 Keys / Secret Keys 03 Symmetric Cryptography 04 Encryption 05 MAC / HMAC 06 Pseudo Random Function 07 Asymmetric Cryptography 08 Asymmetric Encryption (RSA) 09 Signatures 10 RSA Signatures 11 DSA Signatures 12 Key Exchanges 13 RSA Key Exchanges 14 DH Key Exchanges 15 Elliptic Curve Cryptography // ADDITIONAL RESOURCES // Asymmetric Cryptography: Practical TLS - free lessons: Practical TLS - full course: // SUPPORT PRACTICAL NETWORKING // If this content benefited you, then here are TOTALLY FREE ways to show your appreciation: - 👍 Like to help this video reach more viewers - 💬 Comment to boost the channel's visibility - 🔔 Subscribe to help me attract sponsors (this is the number they care about)
- 26720Просмотров
- 1 год назадОпубликованоPractical Networking
Elliptic Curve Cryptography in less than 5 minutes
Похожее видео
Популярное
16 серия красная гадюка
Valu stupid wife temporada finale series
лёлик и барбарики диск
КРАСНАЯ ГАДЮКА все серии
беззаконник 3
КРАСНАЯ ГАДЮКА 3
Universal 2003 hd
Rayton M01
Я жена вашего мужа
Universal effects
Смешарики титры
timon pumbaa
чиполлино
кофико
poland warsaw metro ride from swietokrzyska
Wb 2018 effects
Крізь помилки минулого
Kion lion king trailer 2026
Умизуми
Зворотний напрямок
Безжалостный гений часть5
Потеряний снайпер
Городской снайпер 3
Universal not scary
Смешари Пин код
Valu stupid wife temporada finale series
лёлик и барбарики диск
КРАСНАЯ ГАДЮКА все серии
беззаконник 3
КРАСНАЯ ГАДЮКА 3
Universal 2003 hd
Rayton M01
Я жена вашего мужа
Universal effects
Смешарики титры
timon pumbaa
чиполлино
кофико
poland warsaw metro ride from swietokrzyska
Wb 2018 effects
Крізь помилки минулого
Kion lion king trailer 2026
Умизуми
Зворотний напрямок
Безжалостный гений часть5
Потеряний снайпер
Городской снайпер 3
Universal not scary
Смешари Пин код
Новини