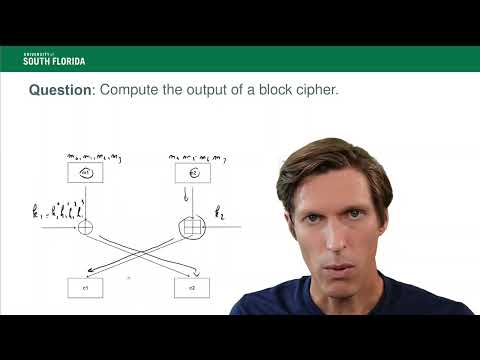
In this video you will learn how to compute the advantage of an adversary in the semantic security game. We use a stream cipher with a PRG that was analyzed (and proven insecure) in the skills video on PRGs.
- 783Просмотров
- 2 года назадОпубликованоUSF Crypto Center