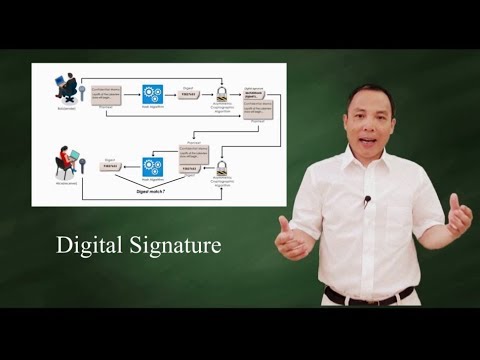
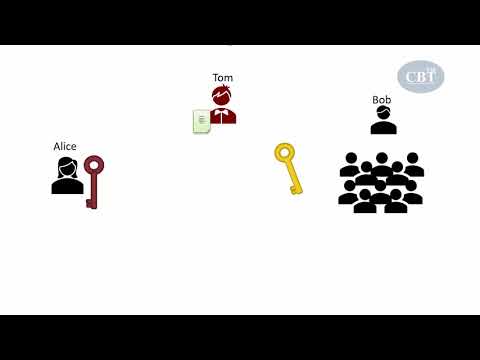
In this video we take a look at Digital Signatures. We explain what they are, show you examples of what types of things are signed, and discuss how they provide Integrity and Authentication to what is signed. We then compare them to HMACs and MACs, which also provide Integrity & Authentication, but have a slightly different use case. // CHAPTERS 0:00 - Intro 0:12 - Simple Definition 0:38 - Signatures are created with Private Key & verified with Public Key 1:31 - Anything can be signed 2:04 - Integrity and Authentication 2:39 - Signatures vs MACs / HMACs 4:23 - Signature Algorithms - RSA DSA // FULL SERIES - Cryptography Essentials // This video is part of a 16-part series covering the essentials of modern Cryptography. Explained simply, and technically accurate. The full series is available here: 📋 ( or use the shortcut ) 00 Series Introduction 01 Hashing 02 Keys / Secret Keys 03 Symmetric Cryptography 04 Encryption 05 MAC / HMAC 06 Pseudo Random Function 07 Asymmetric Cryptography 08 Asymmetric Encryption (RSA) 09 Signatures 10 RSA Signatures 11 DSA Signatures 12 Key Exchanges 13 RSA Key Exchanges 14 DH Key Exchanges 15 Elliptic Curve Cryptography // ADDITIONAL RESOURCES // // SUPPORT PRACTICAL NETWORKING // If this content benefited you, then here are TOTALLY FREE ways to show your appreciation: - 👍 Like to help this video reach more viewers - 💬 Comment to boost the channel's visibility - 🔔 Subscribe to help me attract sponsors (this is the number they care about)
- 8613Просмотров
- 1 год назадОпубликованоPractical Networking
Signatures - What and why are they?
Похожее видео
Популярное
Handy manny Russisch
Красная гадюка 16 серия
Баскервиллей
мультик
красная гадюка 17-20 серия
184
Лихач 3 сезон 1-4
undefined
Потерянный снайпер 2 часть
красный тигр-1
смешарики
Dino Dan where the dinosaurs are
Поерянный снайпер
безжалостный гений 5сезон
губка боб бабуся
Universal pictures effects
союзмультфильм диск
Красная гадюка 2
Animal racing lion game
випуск
Eipril
Тверская 2 сезон
poterianij snaiper 3 seria
ШАРЛОТТА ЗЕМЛЯНИКА
Красная гадюка 16 серия
Баскервиллей
мультик
красная гадюка 17-20 серия
184
Лихач 3 сезон 1-4
undefined
Потерянный снайпер 2 часть
красный тигр-1
смешарики
Dino Dan where the dinosaurs are
Поерянный снайпер
безжалостный гений 5сезон
губка боб бабуся
Universal pictures effects
союзмультфильм диск
Красная гадюка 2
Animal racing lion game
випуск
Eipril
Тверская 2 сезон
poterianij snaiper 3 seria
ШАРЛОТТА ЗЕМЛЯНИКА
Новини