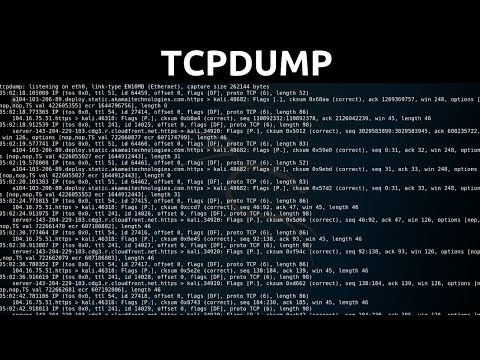
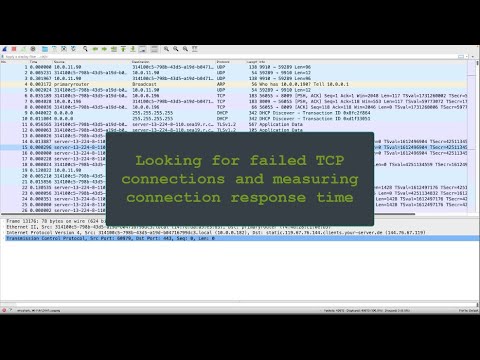
In this tutorial, I will be using Wireshark to analyze my captured network packets using display filters to fitler source ( ) and destination ( ) IP addresses, and #. I will be attempting to find the following 11 packets in the file .pcap file: A FTP packet sourced from your Client showing the Username A FTP packet sourced from your Router 2 showing the username A SSH response from your Linux Server to your Client A SSH response from your Router to your Router 2 An IIS request from your Router 2 and the sequential response from your Windows Server (2 Packets) 4 Packets representing a completed DHCP Process – DISCOVER, REQUEST, OFFER, ACK(4 Packets) An MySQL packet from client to Linux Server. Mark the required packets, then export the required marked captured network packets to new pcap file. Wireshark is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic. Wireshark development thrives thanks to the volunteer contributions of networking experts around the globe. Features of Wireshark including: Deep inspection of hundreds of protocols, with more being added all the time Live capture and offline analysis Multi-platform: Runs on Windows, Linux, macOS Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility The most powerful display filters in the industry Read/write many different capture file formats: such as tcpdump, Pcap NG, Microsoft Network Monitor, etc. Live data can be read from Ethernet, Bluetooth, USB, Token Ring, Frame Relay, etc. Coloring rules can be applied to the packet list for quick, intuitive analysis Thank you for watching! Like & Subscribe!
- 6486Просмотров
- 5 лет назадОпубликованоTechnoConfig
Use Wireshark to Analyze Network Traffic | tcpdump - Pcap
Похожее видео
Популярное
2х2 лёлик и барбарики
макс и катя
РОЖДЕСТВО С КАЮ
mia malkova hot tub
Дельфин 4
Дельфин все серии
Universal sponge effects 1.000
Universal effects g major 16
Красная гадюка 11 серия
ШПИОН И ШЛЯПЫ КОРОЛЕВЫ
Pedernal
ангелина
Потерянный снайпер 9 серия
Самсам
ису или борьку
flip the frog the goal rush
союзмультфильм
dora
Красная гадюка 8 серия
I Built the Worlds smallest V8 Engine
poterianij snaiper 2 seria
Cp
ВАЗА И МПЕРАТОРА
СТРАЖИ ПРАВОСУДИЯ 4
макс и катя
РОЖДЕСТВО С КАЮ
mia malkova hot tub
Дельфин 4
Дельфин все серии
Universal sponge effects 1.000
Universal effects g major 16
Красная гадюка 11 серия
ШПИОН И ШЛЯПЫ КОРОЛЕВЫ
Pedernal
ангелина
Потерянный снайпер 9 серия
Самсам
ису или борьку
flip the frog the goal rush
союзмультфильм
dora
Красная гадюка 8 серия
I Built the Worlds smallest V8 Engine
poterianij snaiper 2 seria
Cp
ВАЗА И МПЕРАТОРА
СТРАЖИ ПРАВОСУДИЯ 4
Новини