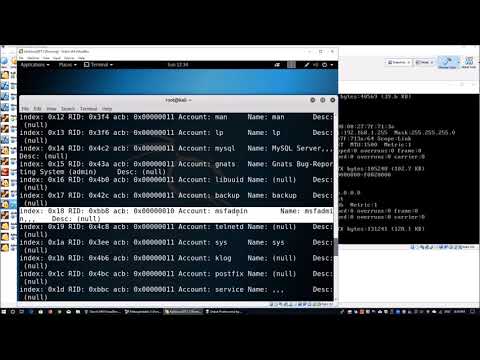
Hackers can access sensitive files through misconfigured SMB shares, no password required! In this step-by-step walkthrough, we’ll demonstrate how anonymous access to SMB (Server Message Block) can expose an entire system. Using the Hack The Box machine "Dancing", we simulate a real-world SMB hacking scenario from enumeration to exploitation using smbclient. Whether you're a cybersecurity student, preparing for the OSCP, or just curious about how SMB works, this video will guide you through the core concepts and tools you need to know. 🚨 This video is for educational and awareness purposes only. ▬▬ Tools Used ▬▬ - Kali Linux (Attacker Machine) - Hack The Box - Dancing Machine (Victim) - Nmap Port Scanner ▬▬ ⏱️ Chapters ▬▬ 0:00 Intro: Why SMB Can Be Dangerous 0:15 What is SMB and How It Works 1:23 Nmap Scan & Open Ports 3:02 Listing SMB Shares (Anonymous Access) 9:07 Exploring SMB Shares Without Credentials 8:10 Gaining Access to WorkShares Folder 11:19 Finding the Flag & Wrapping Up #cybersecurity #penetrationtesting #smb Become a Neurix member @UCUOlY1VUTHMdkLph5ORHF2Q
- 8964Просмотров
- 5 месяцев назадОпубликованоEthical Hacker Diaries
How Hackers Steal Windows Files Using SMB Exploit!
Похожее видео
Популярное
war thunder tech tree
улица далматинцев 101
Tutti fruti kids song
Потерянный снайпер 2снрия
КОТ В ШЛЯПЕ
Preview 2 stars in the sky extended^4
маленькая девочка
Машаимедведь
C p
смешарики барбарики
Illumination 2024
красная гадюка 3 серия
пупок женщины
Thiruttu payale amala paul
Preview 2 stars in the sky v7
ТЁМА И ЛИЗА СТРОЯТ
тарзан фильм
Поточний снайпер 2 часть
Naked yoga
безжалостный гений 5сезон
ЛУЧШИЕ ГЕРОИ НА ТИЖИ
Красная гадюка 2сезон
Youtube
улица далматинцев 101
Tutti fruti kids song
Потерянный снайпер 2снрия
КОТ В ШЛЯПЕ
Preview 2 stars in the sky extended^4
маленькая девочка
Машаимедведь
C p
смешарики барбарики
Illumination 2024
красная гадюка 3 серия
пупок женщины
Thiruttu payale amala paul
Preview 2 stars in the sky v7
ТЁМА И ЛИЗА СТРОЯТ
тарзан фильм
Поточний снайпер 2 часть
Naked yoga
безжалостный гений 5сезон
ЛУЧШИЕ ГЕРОИ НА ТИЖИ
Красная гадюка 2сезон
Youtube
Новини