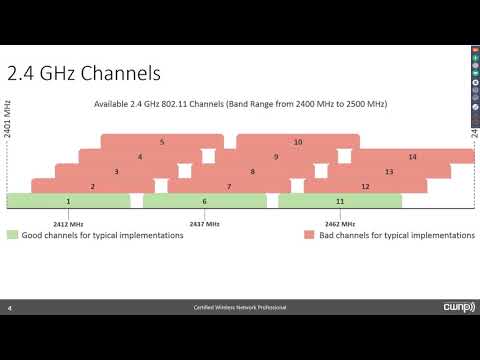
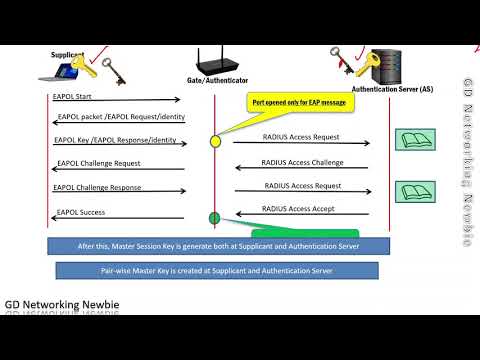
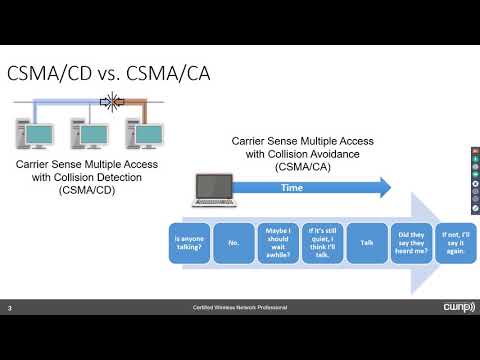
A walk through wireless authentication using both WPA/WPA2 PSK and , and a look at where our encryption keys come from.
- 96098Просмотров
- 1 десятилетие назадОпубликованоBrett Hill
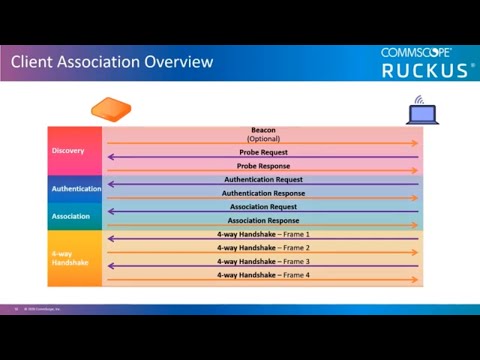
Wireless Authentication and Key Generation
Похожее видео
Популярное
Волчий берег11серии
5 серия красная гадюка
Потеряный снайпер 2 серия
Красная гадюка 6 часть
Цена отказа 7-8 серии
Красная гадюка 4серия
красная гадюка 12
городской снайпер 8 серия
Краснаямгадюка 2 сезон
Стражи правосуддя 5
красная гадюка 7 часть
Красная гадюка 11-16 серии
Lying ear picking
Свинка пеппа
клуб микки мауса
Тверская 2 сезон
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
Big cats size comparison
sewing cozy
КРАСНАЯ ГАДЮКА 15серия
Барбоскины Лучший день
Красный тарантул 3
НЕПОСЕДА ЗУ
потеряій снайпер 5 серия
5 серия красная гадюка
Потеряный снайпер 2 серия
Красная гадюка 6 часть
Цена отказа 7-8 серии
Красная гадюка 4серия
красная гадюка 12
городской снайпер 8 серия
Краснаямгадюка 2 сезон
Стражи правосуддя 5
красная гадюка 7 часть
Красная гадюка 11-16 серии
Lying ear picking
Свинка пеппа
клуб микки мауса
Тверская 2 сезон
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
Big cats size comparison
sewing cozy
КРАСНАЯ ГАДЮКА 15серия
Барбоскины Лучший день
Красный тарантул 3
НЕПОСЕДА ЗУ
потеряій снайпер 5 серия
Новини