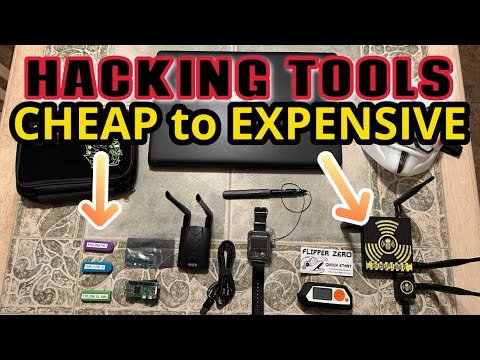
I built my own USB Rubber Ducky using a $15 Raspberry Pi Zero and in this video, I show exactly how hackers use devices like this in real HID attacks. A USB Rubber Ducky is a tiny device that pretends to be a keyboard. Because computers trust keyboards by default, these devices are very dangerous. In this video, I break down how Rubber Duckies work, how I built my Ducky Pi, and why HID-based attacks are something every defender should understand. I also show 3 real demos (with the typing slowed in the script so you can actually see what’s happening). The real payload fires almost instantly. If you're learning cybersecurity, ethical hacking, red teaming, or you love Raspberry Pi projects, this is a great intro to physical access attacks, HID payloads, and how to protect your environment. ⏱️ Timestamps 0:00 – The innocent-looking Pi that can take over a PC 0:25 – What a Rubber Ducky really is & How HID attacks work 1:35 – Demo #1 (Notepad payload) 1:49 – Demo #2 (PowerShell payload) 2:03 – Demo #3 (Fun payload) 2:19 – Lessons learned & Hypothetical 3:05 – Why defenders MUST understand HID attacks 3:23 – How to build your own Ducky Pi 🔗 Build It Yourself (GitHub): LINK IN COMMENT ⚠️ Ethical Reminder Only use devices like this on systems you own or have explicit permission to test. This is for education and awareness, nothing more. 📢 Want More Cybersecurity Content? Subscribe for DIY builds, hacking tool breakdowns, blue-team insights, and real-world cyber examples. 📺 Next up: New videos coming soon!
- 304Просмотров
- 2 недели назадОпубликованоJosiah Golden
How Hackers Use USB Rubber Duckies (I Built One to Show You)
Похожее видео
Популярное
Потерянный снайпер 6серия
Видео потеряный снайпер
малыш вилли 03
Грань правосудия 4сезон
бен 10 реклама
Go Diego go
6серия
Малышарики
Родрі
Барбоскины Лучший день
Numberblock1 grounded
the 70s show
Городской снайпер
КОТ В ШЛЯПЕ
красный тарантул
Игра снайпера 2
Волчий берег все серии
Красная гадюка 5часть
гача лайф
мода из комода
Потерянии снайпер 2
Universal not scary in Luigi group
Безжалостный гений 3
184
Видео потеряный снайпер
малыш вилли 03
Грань правосудия 4сезон
бен 10 реклама
Go Diego go
6серия
Малышарики
Родрі
Барбоскины Лучший день
Numberblock1 grounded
the 70s show
Городской снайпер
КОТ В ШЛЯПЕ
красный тарантул
Игра снайпера 2
Волчий берег все серии
Красная гадюка 5часть
гача лайф
мода из комода
Потерянии снайпер 2
Universal not scary in Luigi group
Безжалостный гений 3
184
Новини