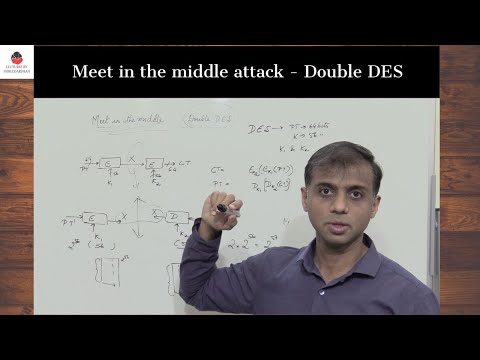
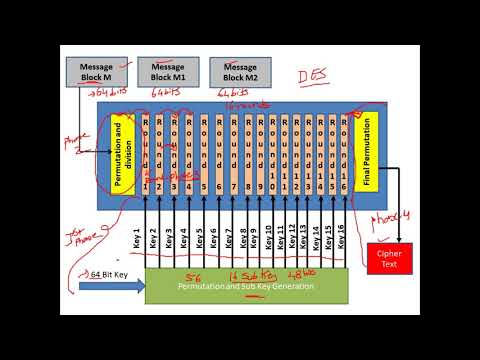
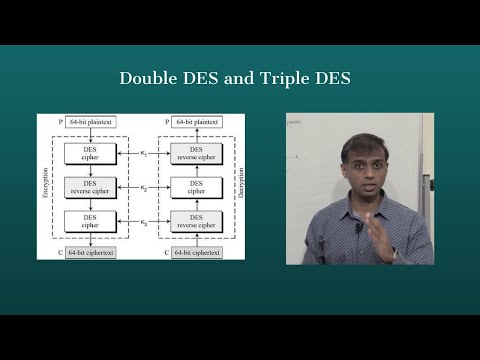
S-DES Encryption || Simplified data encryption standard(S-DES) || - Encryption Algorithm explained with an example 1] s-DES Key Generation: 2] s-DES Encryption : 3] s-DES Decryption : #Cryptography #SDES #Encryption #Decryption #SDES #DataEncryptionStandard #sBox #Confusion #Diffusion #Cipher #SymmetricCipher #cybersecurity Thanks for watching. Do like , share and subscribe 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 𝐁𝐨𝐨𝐤𝐬 𝐈 𝐡𝐚𝐯𝐞 𝐚𝐮𝐭𝐡𝐨𝐫𝐞𝐝: 𝐁𝐡𝐚𝐫𝐚𝐭𝐢𝐲𝐚 𝐊𝐚𝐭𝐡𝐚 𝐕𝐚𝐢𝐛𝐡𝐚𝐯𝐚 - 𝐕𝐨𝐥 𝟏 , 𝟐 , 𝟑 , 𝟒 𝐅𝐨𝐫 𝐛𝐮𝐥𝐤 𝐨𝐫𝐝𝐞𝐫𝐬 𝐚𝐧𝐝 𝐝𝐢𝐬𝐜𝐨𝐮𝐧𝐭𝐬 𝐃𝐌 𝐄𝐦𝐚𝐢𝐥 : 𝐞𝐝𝐮𝐦𝐢𝐭𝐫𝟒𝐮@𝐠𝐦𝐚𝐢𝐥.𝐜𝐨𝐦 𝐓𝐨 𝐛𝐮𝐲 𝐛𝐨𝐨𝐤𝐬 𝐨𝐧 𝐀𝐦𝐚𝐳𝐨𝐧: Volume 1: Volume 2: Volume 3: Volume 4: 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 𝐌𝐲 𝐒𝐨𝐜𝐢𝐚𝐥 𝐌𝐞𝐝𝐢𝐚 𝐇𝐚𝐧𝐝𝐥𝐞𝐬 Facebook Page: Telegram (Engineering) : Telegram (Class 10) : Instagram (Education) : Instagram (Hinduism & Spirituality) : Blog : YouTube Channel (Hinduism & Spirituality) : 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 📚 𝐈𝐦𝐩𝐨𝐫𝐭𝐚𝐧𝐭 𝐂𝐨𝐮𝐫𝐬𝐞 𝐏𝐥𝐚𝐲𝐥𝐢𝐬𝐭 📚 𝟏] 𝐂𝐫𝐲𝐩𝐭𝐨𝐠𝐫𝐚𝐩𝐡𝐲 : 𝟐] 𝐃𝐢𝐠𝐢𝐭𝐚𝐥 𝐄𝐥𝐞𝐜𝐭𝐫𝐨𝐧𝐢𝐜𝐬 : 𝟑] 𝐄𝐥𝐞𝐜𝐭𝐫𝐨𝐧𝐢𝐜𝐬 (𝟏𝐬𝐭 𝐘𝐞𝐚𝐫 - 𝐁𝐚𝐬𝐢𝐜) : 𝟒] 𝐄𝐫𝐫𝐨𝐫 𝐂𝐨𝐧𝐭𝐫𝐨𝐥 𝐂𝐨𝐝𝐢𝐧𝐠 : 𝟓] 𝐃𝐢𝐬𝐜𝐫𝐞𝐭𝐞 𝐌𝐚𝐭𝐡𝐞𝐦𝐚𝐭𝐢𝐜𝐬 : 𝟔] 𝐂𝐥𝐚𝐬𝐬 𝟏𝟎 - [𝐂𝐁𝐒𝐄/𝐍𝐂𝐄𝐑𝐓] 𝐌𝐚𝐭𝐡𝐞𝐦𝐚𝐭𝐢𝐜𝐬: 𝟕] 𝐒𝐢𝐠𝐧𝐚𝐥𝐬 𝐚𝐧𝐝 𝐒𝐲𝐬𝐭𝐞𝐦𝐬 : 𝟖] 𝐂𝐨𝐧𝐭𝐫𝐨𝐥 𝐒𝐲𝐬𝐭𝐞𝐦𝐬 : 𝟗] 𝐋𝐢𝐧𝐞𝐚𝐫 𝐀𝐥𝐠𝐞𝐛𝐫𝐚 : 𝟏𝟎] 𝐂𝐥𝐚𝐬𝐬 𝟏𝟐 - 𝐌𝐚𝐭𝐡𝐞𝐦𝐚𝐭𝐢𝐜𝐬 : 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 --------------------------------------------------------------------------------- Blowfish Algorithm : Elliptical Curve Cryptography - 1 : Brute force Attack : Avalanche Effect in Cryptography : Double & Triple DES : Steganography / Cryptography Differences: Four Square Cipher : Route Cipher : Fiestel Cipher Structure: Network Security - Attacks : Network Security - Authentication using Message Encryption : Fiestel Cipher Structure: Diffie Hellman Key Exchange: Euler's Totient Function [Euler's Phi Function]: Fermat's Theorem - Explanation with example: s DES - Key Generation : Differences between s-DES and DES: Primitive Root : -----------------------------------------------------------------------
- 61436Просмотров
- 6 лет назадОпубликованоLectures by Shreedarshan K
S-DES Encryption || Simplified data encryption standard(S-DES) || - Encryption & Decryption
Похожее видео
Популярное
Wonderpt
тарзан фильм
Robinhood sreeleela
Потерянный снайпер 3 серия
FeetSonatina
Фильм потерянный снайпер
Стражи правосудтя
Valu temporada
Потерянный снайпер 6серия
сильвания фэмили реклама
Trade scam script
Темное наследие
Wb 2022 effects
сакс игрушки
oggy
Koktebel
бонифация
dora dasha
врумиз реклама
Universal 2010 g major effects
МАЛЕНЬКАЯ ПРИНЦЕССА
poterianij snaiper 3 seria
Legend of hercules lion
ну погоди 1-16 выпуски
Потерянный снайпер 7 серия
тарзан фильм
Robinhood sreeleela
Потерянный снайпер 3 серия
FeetSonatina
Фильм потерянный снайпер
Стражи правосудтя
Valu temporada
Потерянный снайпер 6серия
сильвания фэмили реклама
Trade scam script
Темное наследие
Wb 2022 effects
сакс игрушки
oggy
Koktebel
бонифация
dora dasha
врумиз реклама
Universal 2010 g major effects
МАЛЕНЬКАЯ ПРИНЦЕССА
poterianij snaiper 3 seria
Legend of hercules lion
ну погоди 1-16 выпуски
Потерянный снайпер 7 серия
Новини