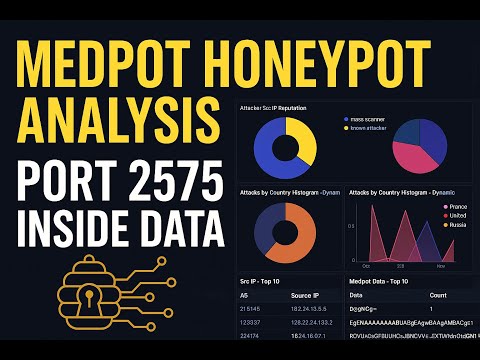
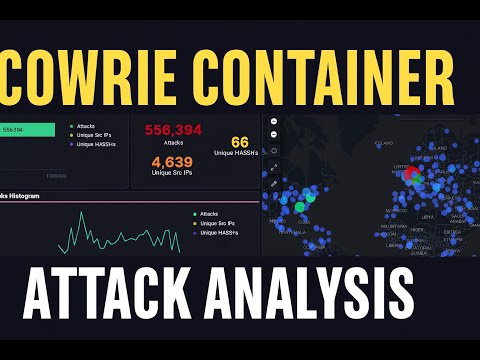
In this video, I explain Heralding in TPot — a powerful honeypot service used to capture attacker behavior across multiple protocols. You’ll learn how Heralding works, which ports it uses, how it performs source IP tracking, and how it logs different protocol interactions from attackers. 🔍 What I Cover in This Video: What is Heralding in the TPot framework Ports used by Heralding How Heralding tracks attackers (Src IP Tracking) Supported protocols (SSH, RDP, HTTP, Telnet, FTP, etc.) Reading the Heralding dashboard Understanding attack logs & authentication attempts Real-time attack map insights This video is perfect for anyone learning: ✔ Cybersecurity ✔ Honeypots ✔ ELK Dashboard Monitoring ✔ Threat Intelligence & Network Security ✔ TPot Installation & SOC Tools 📌 Subscribe for more cybersecurity & TPot tutorials! Heralding TPot TPot honeypot tutorial heralding ports explained honeypot src ip tracking cybersecurity honeypot tools TPot elk dashboard heralding protocols heralding attack logs honeypot monitoring tutorial network security tools
- 4Просмотров
- 2 недели назадОпубликованоTech Journey
Heralding in TPot Explained | Ports, Protocols, Src IP Tracking & Attack Analysis
Похожее видео
Популярное
Tutti fruti kids song
ЛЯПИК ЕДЕТ В ОКИДО
agustin marin low voice i killed wi
forsaken teamers
сваты сезон 1 все серии
стражи провосдия 3 сезон
Diego
Актеры красной гадюки
Etta Mae Hartwell
лёлик и барбарики диск
Красна я гадюка
Preview Disney 2011 effects
ВЕЛОСПОРТ ЮРИЙ ПЕТРОВ .
Бурное безрассудство 2
сваты все серии
Valu stupid wife temporada finale series
красная гадюка сезон 2
Обриси
hentai
Красна я гадюка 5
Pushpa 2 rashmika mandanna
Волчок
Красная гадюка
Я - жена вашого мужа 2
ЛЯПИК ЕДЕТ В ОКИДО
agustin marin low voice i killed wi
forsaken teamers
сваты сезон 1 все серии
стражи провосдия 3 сезон
Diego
Актеры красной гадюки
Etta Mae Hartwell
лёлик и барбарики диск
Красна я гадюка
Preview Disney 2011 effects
ВЕЛОСПОРТ ЮРИЙ ПЕТРОВ .
Бурное безрассудство 2
сваты все серии
Valu stupid wife temporada finale series
красная гадюка сезон 2
Обриси
hentai
Красна я гадюка 5
Pushpa 2 rashmika mandanna
Волчок
Красная гадюка
Я - жена вашого мужа 2
Новини