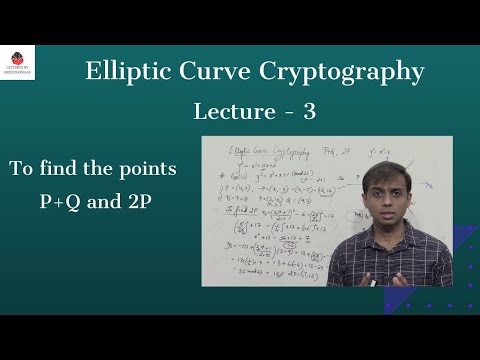
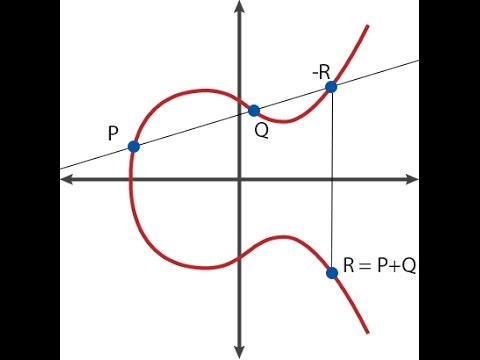
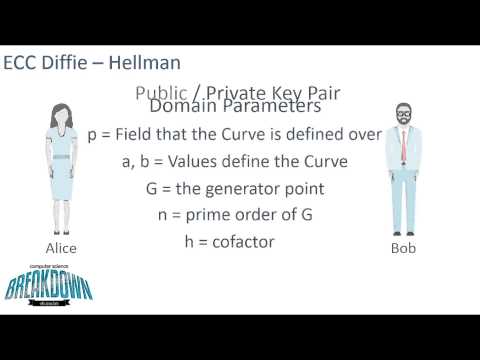
ECC - To find points on the Elliptic Curve ECC in #Cryptography & Security #EllipticCurveCryptography #ECC #Security #NetworkSecurity #Cryptography 1] Elliptic Curve Cryptography | Find points on the Elliptic Curve : 2] Elliptic Curve Cryptography |Encryption and Decryption : 3] Elliptic Curve Cryptography |Find points P+Q and 2P : Thanks for watching. Do like , share and subscribe ------------------------------------------------------------------------------------------------------------ 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 Books I have authored: Bharatiya Katha Vaibhava - Vol 1 , 2 , 3 , 4 For bulk orders and discounts DM To buy books on Amazon: Volume 1: Volume 2: Volume 3: Volume 4: 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 My Social Media Handles Facebook Page: Telegram (Engineering) : Telegram (Class 10) : Instagram (Education) : Instagram (Hinduism & Spirituality) : Blog : YouTube Channel (Hinduism & Spirituality) : 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 📚 Important Course Playlist 📚 1] Cryptography : 2] Digital Electronics : 3] Electronics (1st Year - Basic) : 4] Error Control Coding : 5] Discrete Mathematics : 6] Class 10 - [CBSE/NCERT] Mathematics : 7] Signals and Systems : 8] Control Systems : 9] Linear Algebra : 🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹🔸🔹 ===================================================================== Blowfish Algorithm : Elliptical Curve Cryptography - 1 : Brute force Attack : Avalanche Effect in Cryptography : Double & Triple DES : Steganography / Cryptography Differences: Four Square Cipher : Route Cipher : Fiestel Cipher Structure: Network Security - Attacks : Network Security - Authentication using Message Encryption : Fiestel Cipher Structure: Diffie Hellman Key Exchange: Euler's Totient Function [Euler's Phi Function]: Fermat's Theorem - Explanation with example: s DES - Key Generation : Differences between s-DES and DES: Primitive Root : ----------------------------------------------------------------------- Encryption, Elliptic Curve Cryptography, Decryption, Ciphers, Symmetric Ciphers, Cryptography, Network Security, Polynomials, Primitive root DES Data Encryption Standard Confusion Diffusion Hill Cipher Playfair Cipher Caesar Cipher Hill Cipher Steganography Triple DES Meet in the middle attack Blowfish Algorithm Eulers Theorem Chinese Remainder Theorem IDEA GCD Number Theory
- 50086Просмотров
- 5 лет назадОпубликованоLectures by Shreedarshan K
Elliptic Curve Cryptography | Find points on the Elliptic Curve |ECC in Cryptography & Security
Похожее видео
Популярное
Сериал я жив
FeetSonatina
кошечки собачки
Красная гадюка 16 серия
Игра спайпера 2
снег
Big cats size comparison
tushy
Красна я гадюка 6
Красный тарантул 3
Tutti fruti kids song
бурное безрасудство 1
Заставки Тижи TiJi
Смешарики
5.0 I killed universal pictures
Безжалостный гений
КРАСНАЯ ГАДЮКА 3
agustin marin i killed windows
健屋
Лихач 3 сезон 10-12
Красная гадюка 6
Тротро
Фул школьниц
Никелодеон реклама
FeetSonatina
кошечки собачки
Красная гадюка 16 серия
Игра спайпера 2
снег
Big cats size comparison
tushy
Красна я гадюка 6
Красный тарантул 3
Tutti fruti kids song
бурное безрасудство 1
Заставки Тижи TiJi
Смешарики
5.0 I killed universal pictures
Безжалостный гений
КРАСНАЯ ГАДЮКА 3
agustin marin i killed windows
健屋
Лихач 3 сезон 10-12
Красная гадюка 6
Тротро
Фул школьниц
Никелодеон реклама
Новини