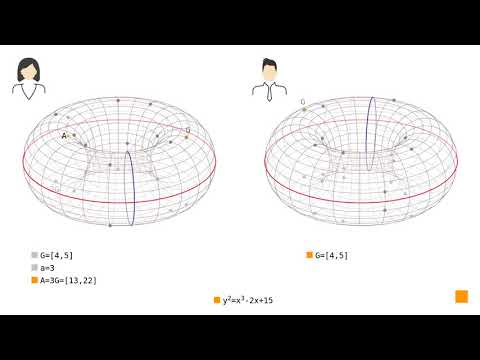
Welcome to "V8d: Elliptic Curve Diffie-Hellman (ECDH)," the fourth lecture in the elliptic curve cryptography (ECC) series from Alfred Menezes's "Crypto 101: Building Blocks" course. In this essential video, you’ll explore the mechanics and applications of ECDH, a crucial protocol for secure key exchange in applied cryptography and widely used across TLS and secure communications. Perfect for computer science students, software engineers, mathematicians, and cybersecurity professionals, this lecture delves deep into how Diffie-Hellman key agreement works on elliptic curves. Gain a clear understanding of the differences between unauthenticated and authenticated ECDH, along with the potential vulnerabilities such as man-in-the-middle attacks and malicious intruder-in-the-middle threats. Learn how ECDH enables forward secrecy, ensuring that session keys remain secure even if long-term keys are compromised—a vital feature in modern secure protocols. This video is ideal for anyone seeking a state-of-the-art, free online course on elliptic curve cryptography and its real-world applications in secure data exchange. Enhance your knowledge and advance your skills in applied cryptography with this foundational ECDH lecture! Lecture playlist: Course web page: The slides are available on the course web page. "Elliptic curve cryptography" chapter from "Textbook of Applied Cryptography": Other cryptography courses: Slides 00:00 Introduction 00:22 Slide 329: Elliptic Curve Diffie-Hellman (ECDH) 01:55 Slide 330: Unauthenticated ECDH 04:51 Maple ECDH example 06:56 Slide 331: Malicious intruder-in-the-middle attack (MITM) 10:13 Slide 332: Authenticated ECDH 12:13 Slide 333: RSA key transport of ECDH in TLS? 15:23 Slide 334: ECDH and forward secrecy 18:52 Slide 335: The ECDH stack 20:02 Coming up
- 872Просмотров
- 1 год назадОпубликованоCryptography 101
V8d: Elliptic Curve Diffie-Hellman (ECDH) (Applied Cryptography 101)
Похожее видео
Популярное
Big cats size comparison
красная гадюка сезон 2
Голие школьниц
Городской снайпер 3
101 далматинец
Актеры красная гадюка 2025
шопкинс реклама
Потеряный снайпер
Красна я гадюка 5
Daily Mail
Preview 2 oh yeah
бен 10
Потераний снайпер 2
хасбро раша операция
dominant
Walt Disney pictures 2011 in g major effects
ZERO FORTY FIVE
Стражи проавосудия 5
Грань правосудия 5
Игра спайпера 2
томас и его друзья джеймс
спагетти макароны
Ози Бу Защити Планету
poland warsaw metro ride from swietokrzyska
Красная гадюка 6 часть
красная гадюка сезон 2
Голие школьниц
Городской снайпер 3
101 далматинец
Актеры красная гадюка 2025
шопкинс реклама
Потеряный снайпер
Красна я гадюка 5
Daily Mail
Preview 2 oh yeah
бен 10
Потераний снайпер 2
хасбро раша операция
dominant
Walt Disney pictures 2011 in g major effects
ZERO FORTY FIVE
Стражи проавосудия 5
Грань правосудия 5
Игра спайпера 2
томас и его друзья джеймс
спагетти макароны
Ози Бу Защити Планету
poland warsaw metro ride from swietokrzyska
Красная гадюка 6 часть
Новини