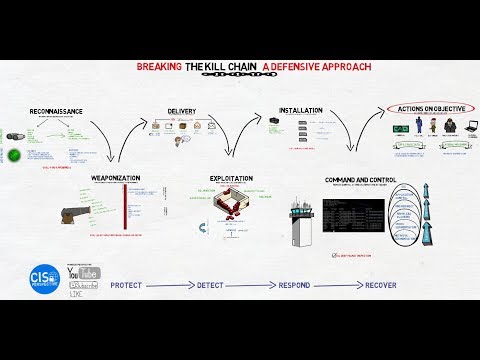
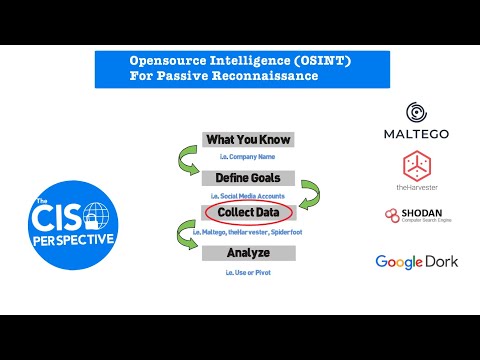
Reconnaissance is the first in the cyber security kill-chain and it involved both passive and active techniques to obtain information about a target. Once an attacker has used Opensource Intelligence (OSINT) for passive reconnaissance, they generally move on to active techniques of information gathering that involve direct interaction with a target. In this video, we'll discuss active the active reconnaissance methodology and review tools and techniques for gathering information we can use for the next step in the kill-chain. Active Reconnaissance Overview, Methodology and Procedures 0:47 DNS Enumeration (dnsrecon & dnsenum) 1:47 SMTP Enumeration (netcat, snip-enum, swaks) 2:54 nMap Port Scanning Using Decoys 3:43 nMap Scripting Engine (NSE) 5:49 👇 More Info 👇 Animations by TCP Media: Viral content. Tech-first thinking. White-glove service. 🎯 Need content like this? Visit for high-impact technical marketing.
- 9588Просмотров
- 5 лет назадОпубликованоThe CISO Perspective
Cyber security Kill Chain: Active Reconnaissance Overview, Methodology and Tools
Похожее видео
Популярное
Preview 2 stars in the skynded^4
красная гадюка 7 часть
ГРАНЬ ПРАВОСУДИЯ
Fap teen
Крізь помилки минулого
Червона гадюка 16 серія
бен 10
Красная гадюка 6 серия
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
Лихач 2025
klaskyklaskyklasskyklasky joey 2 do go
Preview universal prisma
скорей скорей
Дорама вечная любовь
майя сказочница
красный тарантул
Актеры красной гадюки
Секс и дзен 1
jarmies
чужой район 2 сезон
Фул школьниц
RafałBrzozowski
КРАСНАЯ ГАДЮКА все серии
Big cats size comparison
Handy manny Russisch
красная гадюка 7 часть
ГРАНЬ ПРАВОСУДИЯ
Fap teen
Крізь помилки минулого
Червона гадюка 16 серія
бен 10
Красная гадюка 6 серия
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
Лихач 2025
klaskyklaskyklasskyklasky joey 2 do go
Preview universal prisma
скорей скорей
Дорама вечная любовь
майя сказочница
красный тарантул
Актеры красной гадюки
Секс и дзен 1
jarmies
чужой район 2 сезон
Фул школьниц
RafałBrzozowski
КРАСНАЯ ГАДЮКА все серии
Big cats size comparison
Handy manny Russisch
Новини