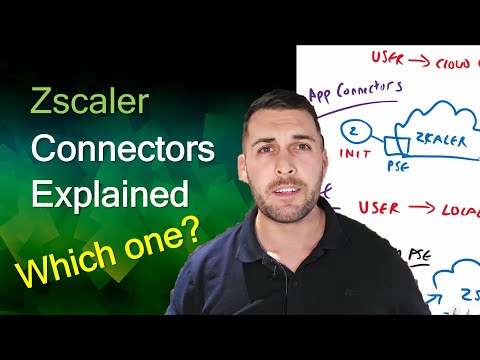
In this video, I break down how Zscaler actually works — from the Zero Trust Exchange architecture to the Zscaler Client Connector and data flow through ZIA and ZPA. Using a virtual whiteboard, I map out how Zero Trust access works in the real world: securing users, devices, and applications no matter where they are. You’ll learn: ➤ What the Zero Trust Exchange really is (and isn’t) ➤ How ZIA and ZPA secure and inspect traffic ➤ How ZDX and DLP add visibility and control ➤ Why Zero Trust is redefining enterprise security Perfect for IT pros, network engineers, and anyone curious about how Zero Trust actually functions behind the buzzwords. If you find this helpful, hit Like, Subscribe, and share it with your team — let’s demystify Zero Trust together. #Zscaler #ZeroTrust #CyberSecurity #CloudSecurity #ZIA #ZPA #ZDX #DataLossPrevention #NetworkSecurity #InfoSec #ZeroTrustExchange #CloudArchitecture #ZTNA #SASE #DigitalExperience #SecurityEngineering #ITSecurity #CloudNetworking #TechExplained #WhiteboardSession "Please note that the content in these videos does not constitute formal advice and is not affiliated with any third-party company. For official, vendor-backed guidance, always consult the relevant documentation and support channels. These videos are intended purely as informal discussions to provide general help and insight."
- 5532Просмотров
- 2 месяца назадОпубликованоTom Talk Tech
How Zscaler Works: The Zero Trust Exchange Explained (ZIA, ZPA, ZDX & DLP) - Simple Whiteboard 101
Похожее видео
Популярное
Eipril
неумолимый 3
Anny_6Feet10
FeetSonatina
веселая-карусел-24
барбоскины обзор диск
Деревяшки
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
бурное безрасудство 1
Пим и пэм
Darn David house
RafałBrzozowski
Universal weird code
Кормление
Потериани снаипер 3 серя
настя девочки
Koktebel
Умизуми
Youtube
Фивел
маленький шеф карусель
Свинка пеппа
Поточний снайпер 2 часть
Бурное безрассудство2
неумолимый 3
Anny_6Feet10
FeetSonatina
веселая-карусел-24
барбоскины обзор диск
Деревяшки
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
бурное безрасудство 1
Пим и пэм
Darn David house
RafałBrzozowski
Universal weird code
Кормление
Потериани снаипер 3 серя
настя девочки
Koktebel
Умизуми
Youtube
Фивел
маленький шеф карусель
Свинка пеппа
Поточний снайпер 2 часть
Бурное безрассудство2
Новини