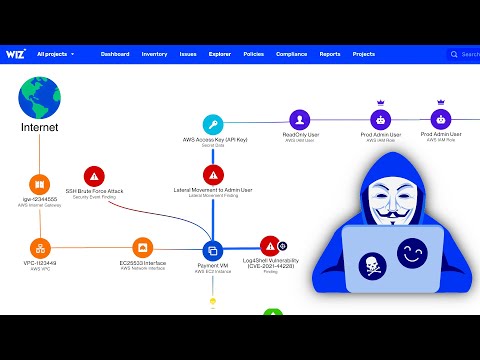
Managing who can access what within an organization is one of the most critical aspects of cybersecurity. Even if strong authentication keeps attackers out, granting excessive or poorly managed permissions can still expose sensitive systems and data to misuse—whether intentional or accidental.
- 14Просмотров
- 1 неделя назадОпубликованоCipher Knights Academy
Lab Guide: Building an AD & DNS Lab
Похожее видео
Популярное
Обриси
Потеряный снайпер 1
Картоплини та дракони
Чудо
Universal effects in conga busher
незнайка за рулем
ПОТЕРЯННЫЙ СНАЙПЕР2
ису или борьку
Красная гадюка 4 серия
Angela White
ЛЯПИК ЕДЕТ В ОКИДО
Темное наследие
Лихач 2025
poterianij snaiper 3 seria
хулиган и пай девочка
Nick jr
Дельфин 3
Eipril
ну погоди 18 выпуск
forsaken fandom
Daily Mail
cum
Tantric awakening shaft
Красная гадюка часть 3
Городской снайпер 3
Потеряный снайпер 1
Картоплини та дракони
Чудо
Universal effects in conga busher
незнайка за рулем
ПОТЕРЯННЫЙ СНАЙПЕР2
ису или борьку
Красная гадюка 4 серия
Angela White
ЛЯПИК ЕДЕТ В ОКИДО
Темное наследие
Лихач 2025
poterianij snaiper 3 seria
хулиган и пай девочка
Nick jr
Дельфин 3
Eipril
ну погоди 18 выпуск
forsaken fandom
Daily Mail
cum
Tantric awakening shaft
Красная гадюка часть 3
Городской снайпер 3
Новини