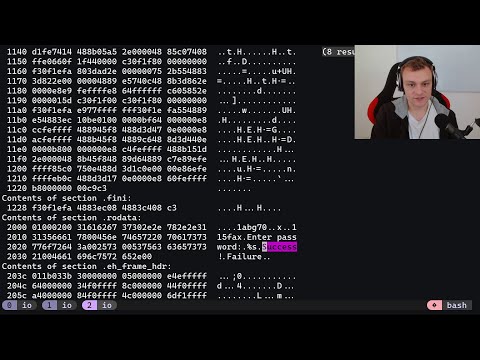
Linux memory analysis is a well known and researched topic. You're likely familiar with many tools that allow us to capture memory from a Windows system. But, have you ever wondered memory capture process for Linux system? And how can you analyze them using Volatility? Well, wait no longer, because that's exactly what we'll cover in this episode! I will show you the easiest process to perform memory capture for a Linux system and how to prepare your volatility tool to parse that memory dump to extract valuable information at the time of doing forensics investigation! In today's episode I have tried to show you from scratch how can you analyze the memory of an infected Linux machine. What are the basic steps, basic plugins, how they differ from windows and how to pivot from one analytics to another. 👉Watch this episode- for creation of Linux Kernel profile for volatility. WATCH BELOW Playlists as well, if you want to make your career in DFIR and Security Operations!! ------------------------------------------------------------------------------------------------------------------------- INCIDENT RESPONSE TRAINING Full Course 👉 DFIR Free Tools and Techniques 👉 Windows and Memory Forensics 👉 Malware Analysis 👉 SIEM Tutorial 👉 Threat Hunt & Threat Intelligence 👉 Threat Hunt with Jupyter Notebook👉 📞📲 FOLLOW ME EVERYWHERE- ------------------------------------------------------------------------------------------------------------------------- ✔ LinkedIn: ✔ You can reach out to me personally in LinkedIn as well- ✔ Twitter: @blackperl_dfir ✔ Git: ✔ Insta: (blackperl_dfir) ✔ Can be reached via support@ 🙏Credit- ------------------------------------------------------------------------------------------------------------------------- The sample memory image and this episode is influenced by the CTF prepared by 2phi and Nofix on CyberDefenders Platform. Huge Shout out to the Team for preparing this challenge. You can practice and complete the challenge from here- The answers need to be obtained by yourself and none of them have been provided here in this episode!
- 7247Просмотров
- 3 года назадОпубликованоBlackPerl
Linux Memory Analysis with Volatility- 101, Compromised Linux System
Похожее видео
Популярное
Обризи
mickey mouse clubhouse
Dora the explorer
Смешари Пин код
Koktebel
Universal dement
взлом карусели
Профиссионал
agustin marin low voice i killed wi
flip the frog the goal rush
Menu dvd Lex olivie remake monstros sa
Крізь помилки минулого
peeping on jewish girls
moden toking
Dia de piscina com as meninas
Грань правосудия 4сезон
20 x fulle episodar
Красная гадюка 16 серия
безжалостный гений 5сезон
16 серия красная гадюка
Wb 2002
мальчики
Wb 2002 effects
Даша-следопыт - Даша ковбой
agustin marin i killed windows
mickey mouse clubhouse
Dora the explorer
Смешари Пин код
Koktebel
Universal dement
взлом карусели
Профиссионал
agustin marin low voice i killed wi
flip the frog the goal rush
Menu dvd Lex olivie remake monstros sa
Крізь помилки минулого
peeping on jewish girls
moden toking
Dia de piscina com as meninas
Грань правосудия 4сезон
20 x fulle episodar
Красная гадюка 16 серия
безжалостный гений 5сезон
16 серия красная гадюка
Wb 2002
мальчики
Wb 2002 effects
Даша-следопыт - Даша ковбой
agustin marin i killed windows
Новини