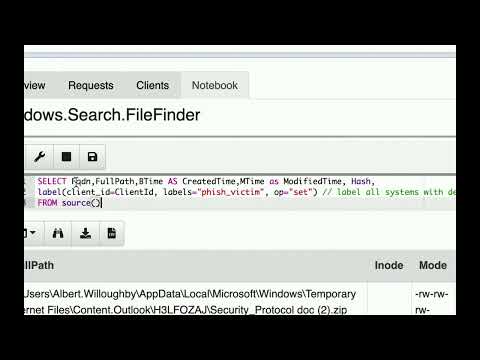
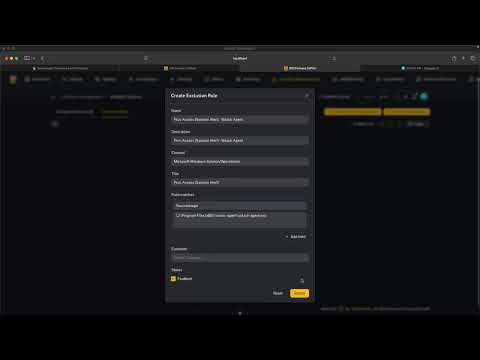
In this tutorial, we solve a common challenge in open-source cybersecurity: integrating Sigma detection rules into an existing SIEM stack without manual conversions or heavy log ingestion overhead. We’ll walk through setting up Velociraptor to run Sigma rules directly on Windows endpoints, scheduling regular scans, excluding noisy detections, and forwarding alerts to Copilot for seamless incident management. By the end, you’ll see how Velociraptor’s built-in Sigma capabilities can supercharge threat detection—no more manual Sigma translations needed. Blog Post: Velociraptor SIGMA Artifact Pack: Get started with CoPilot at: 👨🏻💻 Professional Services: 👾 Discord Channel:
- 3311Просмотров
- 8 месяцев назадОпубликованоTaylor Walton
Supercharge Open-Source Cybersecurity: Velociraptor + Sigma for Your SIEM
Похожее видео
Популярное
Никелодеон
Tschu tschu wa
سكس
красный тарантул 3сезон
Лихач 7-9
VESELAYA-KARUSEL-12
Backyardigans escape de la aldea magica
КРАСНАЯ ГАДЮКА 3
undefined
Noddy
неумолимый 3
Фивел
Jingle bells kids song
Потеряный снайпер 3 серия
макс и катя тележка
Секс и дзен 1
ЛЕТНИЕ КАНИКУЛЫ С СИДОМ
потерянній снайпер
Даша
Porn. Ideas
Лихач 2025
Naked yoga
Родрі
красный тарантул
Сериал я жив
Tschu tschu wa
سكس
красный тарантул 3сезон
Лихач 7-9
VESELAYA-KARUSEL-12
Backyardigans escape de la aldea magica
КРАСНАЯ ГАДЮКА 3
undefined
Noddy
неумолимый 3
Фивел
Jingle bells kids song
Потеряный снайпер 3 серия
макс и катя тележка
Секс и дзен 1
ЛЕТНИЕ КАНИКУЛЫ С СИДОМ
потерянній снайпер
Даша
Porn. Ideas
Лихач 2025
Naked yoga
Родрі
красный тарантул
Сериал я жив
Новини