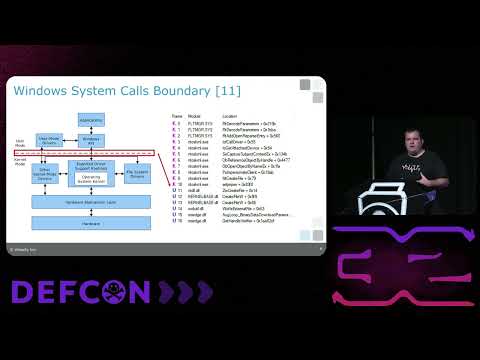
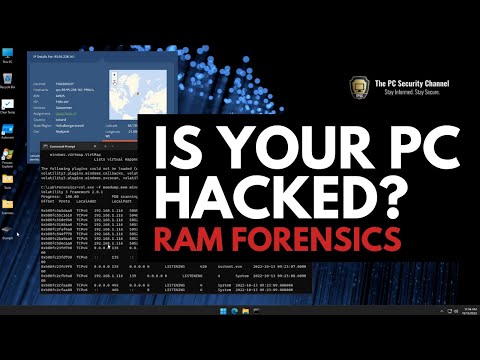
What if there was a better way? What if examiners could get to critical data quicker? What if the digital data could inform the interview questions? Typically, investigators do not collect or analyze memory in criminal/end-user investigations. Acquiring and analyzing memory is rapid. This means results from the acquisition and analysis of your memory collection can be completed long before the drive finishes imaging. Aaron Sparling, @osintlabworks, Digital Forensics Examiner, Portland Police Bureau Jessica Hyde, Director of Forensics, Magnet Forensics; Adjunct Professor, George Mason University DFIRCON 2020 - Live Online Virtual, US Eastern | Mon, Nov 2 - Sat, Nov 7, 2020 Courses Available: FOR308: Digital Forensics Essentials - NEW FOR498: Battlefield Forensics & Data Acquisition FOR500: Windows Forensic Analysis FOR508: Advanced Incident Response, Threat Hunting, and Digital Forensics FOR518: Mac and iOS Forensic Analysis and Incident Response FOR572: Advanced Network Forensics: Threat Hunting, Analysis, and Incident Response FOR578: Cyber Threat Intelligence FOR585: Smartphone Forensic Analysis In-Depth FOR610: Reverse-Engineering Malware: Malware Analysis Tools and Techniques
- 5759Просмотров
- 5 лет назадОпубликованоSANS Digital Forensics and Incident Response
Making Memories: Using Memory Analysis for Faster Response to User Investigations - SANS DFIR Summit
Похожее видео
Популярное
Wb effects not scary
Сериал красная гадюка 5
Смішарики
Universal 1997 2012 effects
Малыш хиппо
reupload my edited video bb into song version
Ликвидатор Среди Магов
Актеры красной гадюки
Грань правосудия 5
2х2 лёлик и барбарики
masculine men
ШПИОН И ШЛЯПЫ КОРОЛЕВЫ
g major 26 turn normal
poland warsaw metro ride from swietokrzyska
Halloween boo boo song
Nick jr
Вулиця сезам
Красна я гадюка
Потеряний снайпер2
смешарики спорт
потерянный сгайпер
Cartoon network russian
Classic caliou misbehaves on a road
poterianij snaiper 2 seria
Сериал красная гадюка 5
Смішарики
Universal 1997 2012 effects
Малыш хиппо
reupload my edited video bb into song version
Ликвидатор Среди Магов
Актеры красной гадюки
Грань правосудия 5
2х2 лёлик и барбарики
masculine men
ШПИОН И ШЛЯПЫ КОРОЛЕВЫ
g major 26 turn normal
poland warsaw metro ride from swietokrzyska
Halloween boo boo song
Nick jr
Вулиця сезам
Красна я гадюка
Потеряний снайпер2
смешарики спорт
потерянный сгайпер
Cartoon network russian
Classic caliou misbehaves on a road
poterianij snaiper 2 seria
Новини