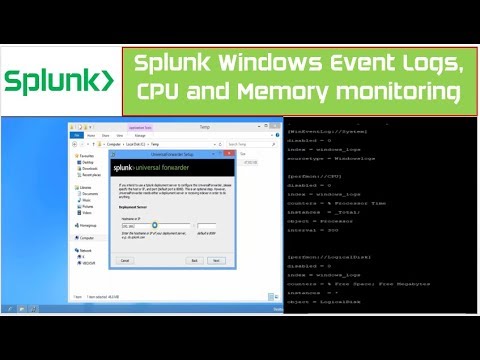
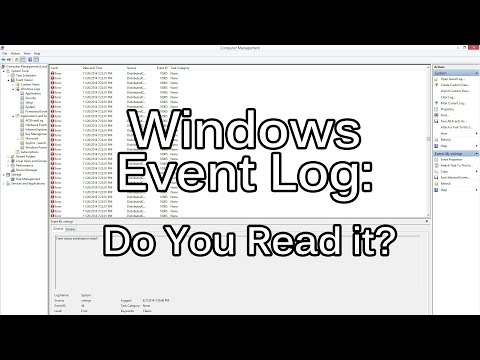
These are the event logs that will help you identify malicious activity on your network. Follow TECH(talk) for the latest tech news and discussion! ---------------------------------- SUBSCRIBE: FACEBOOK: TWITTER: IDG ENTERPRISE WEBSITES Computerworld: CIO: CSO: InfoWorld: Network World:
- 6047Просмотров
- 5 лет назадОпубликованоTECHtalk
Guide to key Windows 10 event logs you need to monitor
Похожее видео
Популярное
Стражи проавосудия 5
Потериани снаипер 3 серя
Фивел
klaskyklaskyklaskyklasky gummy bear g major 26
5 серия красная гадюка
Голие школьниц
Красная гадюка4
гача лайф
Стражи правосудия 3 сезн
Барбоскины Лучший день
Волчок
Bing misbehaves
Etta Mae Hartwell
Красная гадюка 8 серия
Потерянный снайпер 6
Потерянный снайпер 3 серия
МАЛЕНЬКАЯ ПРИНЦЕССА
смешарики
Стрекоза и муравей
барбоскины обзор диск
Потеряний снайпер
Бит и его
Дорогу Нодди
jarmies
красивая музыка
Потериани снаипер 3 серя
Фивел
klaskyklaskyklaskyklasky gummy bear g major 26
5 серия красная гадюка
Голие школьниц
Красная гадюка4
гача лайф
Стражи правосудия 3 сезн
Барбоскины Лучший день
Волчок
Bing misbehaves
Etta Mae Hartwell
Красная гадюка 8 серия
Потерянный снайпер 6
Потерянный снайпер 3 серия
МАЛЕНЬКАЯ ПРИНЦЕССА
смешарики
Стрекоза и муравей
барбоскины обзор диск
Потеряний снайпер
Бит и его
Дорогу Нодди
jarmies
красивая музыка
Новини