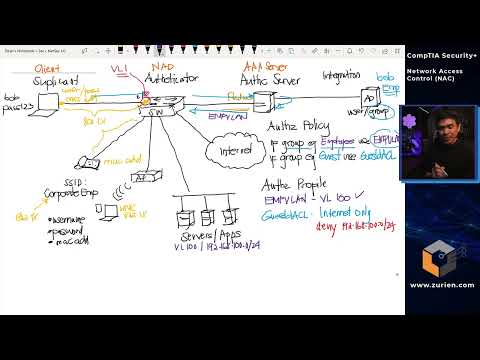
This video discussed the Network Access Control (NAC) including its architecture and components and concepts. Pre-Admission Control 1. System/ User profiling (Agent/Agentless) 2. System/ User Authentication (device profile, captive-P) 3. Compliance/Security Posture Checking (BYOD at Hot-Spot) a. Anti-virus (prevent x-contamination) b. System Patch c. System Configuration d. Auto Remediation Post-Admission Control 1. System/ User Authorization (compliance results) 2. Role-based Access Control (RBAC) - HR to HR Network Deployment Options Inline: All-in-one (Firewall+NAC+Agentless,easy,new) Out-of-Band: (Remote, Agent+Agentless, existing) Quarantine VLAN, Captive Portal, ARP/NDP Poisoning Mobile NAC: Warn if low, Download once WIFI /Wired Advantages 1. Counters Zero-Days Attacks 2. Network AAA, RBAC 3. Enforce Secure Network Protocols (e.g. EAP-TLS) 4. Integration with other Security Tools (NOC/SOC)
- 36189Просмотров
- 5 лет назадОпубликованоCyber Security Entertainment
Network Access Control (NAC)
Похожее видео
Популярное
Потеряний снайпер
Игра спайпера 2
Красная гадюка 17
Улица сезам
Стражи правосудия
Pushpa 2 rashmika mandanna
Красная гадюка 16 серия
jetix
ну погоди 1-16 выпуски
шатун сериал
Профиссионал
настя катя
reupload my edited video bb into song version
веселая-карусел-24
карусель
Красная гадюка 14 серия
Заставки Тижи TiJi
Legend of hercules lion
Грань провосудия 4серия
Никелодеон реклама
малыш вилли 03
Картоплини та дракони
Игра спайпера 2
Красная гадюка 17
Улица сезам
Стражи правосудия
Pushpa 2 rashmika mandanna
Красная гадюка 16 серия
jetix
ну погоди 1-16 выпуски
шатун сериал
Профиссионал
настя катя
reupload my edited video bb into song version
веселая-карусел-24
карусель
Красная гадюка 14 серия
Заставки Тижи TiJi
Legend of hercules lion
Грань провосудия 4серия
Никелодеон реклама
малыш вилли 03
Картоплини та дракони
Новини