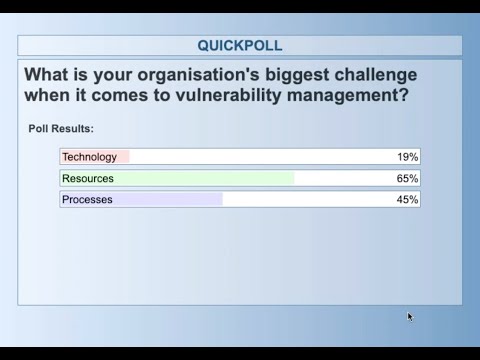
Get in-depth insights into the processes needed for a successful vulnerability management program. This Includes categorisation, prioritisation, and the dissemination of findings to different parts of your organisation. Follow us on LinkedIn: Learn More About Our Vulnerability Management Services:
- 3340Просмотров
- 8 лет назадОпубликованоPhriendly Phishing
How to setup the right processes for vulnerability management
Похожее видео
Популярное
Lying ear picking
Баскервиллей
Big big family
БУРНОЕ БЕЗРАССУДСТВО 3
Красная гадюка фільм 7
Ликвидатор Среди Магов
2х2 лёлик и барбарики
Безжалостный гений
ЛЕТО НА ТИЖИ
Божественний доктор
Он іздевался над женой
Koktebel
Цена отказа 7-8 серии
Disney channel russian
Василь котович
Ози Бу Защити Планету
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
Youtube
Баскервиллей
humiliation
Чупи и Дуду
MickeyMouse
Божественний доктор
чиполлино
Баскервиллей
Big big family
БУРНОЕ БЕЗРАССУДСТВО 3
Красная гадюка фільм 7
Ликвидатор Среди Магов
2х2 лёлик и барбарики
Безжалостный гений
ЛЕТО НА ТИЖИ
Божественний доктор
Он іздевался над женой
Koktebel
Цена отказа 7-8 серии
Disney channel russian
Василь котович
Ози Бу Защити Планету
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
Youtube
Баскервиллей
humiliation
Чупи и Дуду
MickeyMouse
Божественний доктор
чиполлино
Новини