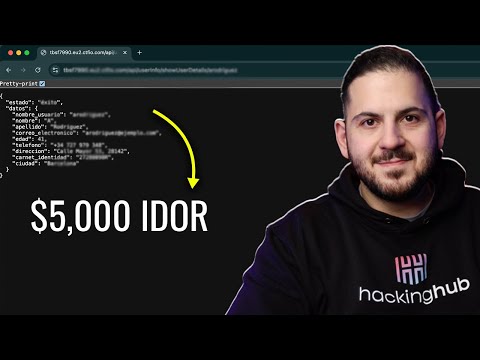
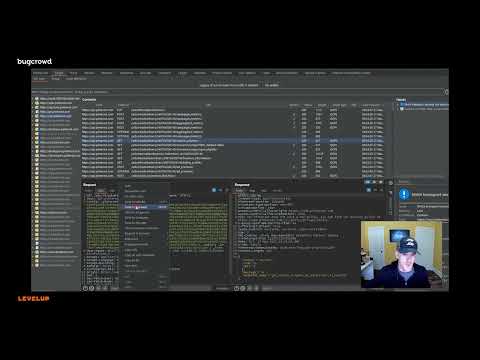
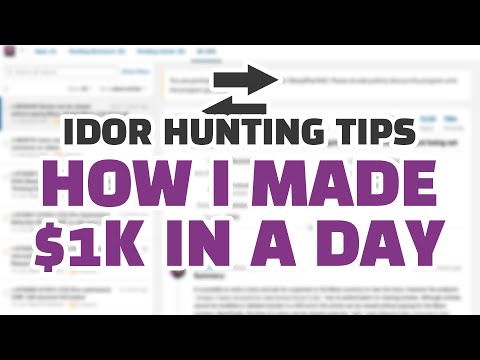
In this video, we demonstrate a proof of concept (PoC) for an Insecure Direct Object Reference (IDOR) vulnerability. Learn how attackers can manipulate URLs or parameters to access unauthorized data or perform actions on a website or application. We'll walk through the exploitation process step by step, showcasing how this vulnerability can be identified and mitigated. Understanding IDOR is crucial for web developers and security professionals to protect sensitive user data from unauthorized access. Stay tuned to see how to recognize and prevent IDOR vulnerabilities in your own applications!" #BugBounty #CyberSecurity #EthicalHacking #WebSecurity #IDOR #HackerLife #PenTesting #SecurityResearch #HackingTips #BugHunter #OWASP #Vulnerability #HackThePlanet #InfoSec #TechTutorial #RedTeam #SecurityExploit #CyberAttack #HackersGonnaHack
- 23001Просмотров
- 9 месяцев назадОпубликованоHey i’m parth
Exploiting IDOR Vulnerability for an $800 Bug Bounty | Bug Bounty | Lets learn Stupid
Похожее видео
Популярное
Дорама вечная любовь
Wb 2002
КОТ В ШЛЯПЕ
веселая-карусел-25
Красная годюка
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
ЛЕТНИЕ КАНИКУЛЫ С СИДОМ
Красная гадюка
Сутінки розділ 3
Красная гадюка 5часть
Universal 1997 2012 g. Major 4
Смешарики
40 или Геометрия любви
Потерянный снайпер 4 серия
navy boat crew
Городской снайпер 2
Universal g major in luig group Mari
oggy
сериал
ну погоди 1-16 выпуски
spit painting
Божественний доктор
Тваринки-Бляшанки
Wb 2002
КОТ В ШЛЯПЕ
веселая-карусел-25
Красная годюка
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
ЛЕТНИЕ КАНИКУЛЫ С СИДОМ
Красная гадюка
Сутінки розділ 3
Красная гадюка 5часть
Universal 1997 2012 g. Major 4
Смешарики
40 или Геометрия любви
Потерянный снайпер 4 серия
navy boat crew
Городской снайпер 2
Universal g major in luig group Mari
oggy
сериал
ну погоди 1-16 выпуски
spit painting
Божественний доктор
Тваринки-Бляшанки
Новини