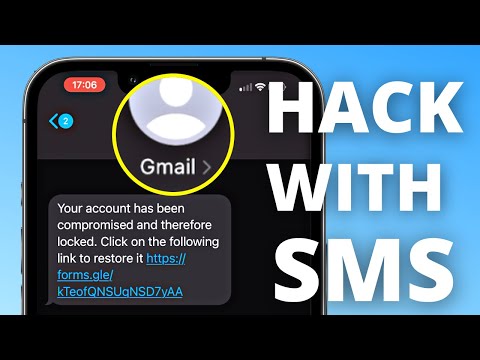
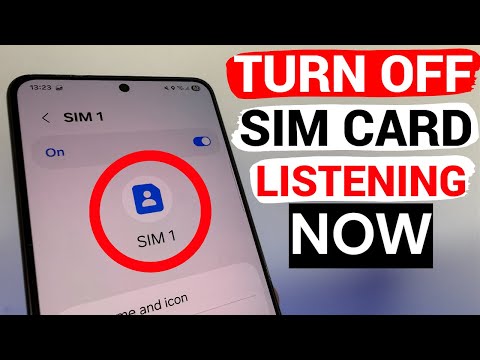
Every SIM-Swap Trick Explained in Detail No service. No texts. No control. If your phone suddenly goes silent and your bank confirms a crypto withdrawal—you’ve just been SIM-swapped. This video breaks down every known SIM swap method, how attackers steal your number, and what you must do to protect your identity, money, and digital life in 2025. ⚠️ What You’ll Learn About SIM Swapping: ✔️ SIM Swap Fraud & Port-Out Scams ✔️ Insider Threats at Mobile Carriers ✔️ Phishing Callbacks & Fake Carrier Messages ✔️ Social Media Scraping & Data Leaks ✔️ eSIM Hijacking & SIM Cloning ✔️ Voicemail Hacking & 2FA Interception ✔️ Malware-Based Identity Theft ✔️ Fake SIM Errors & Callback Interception ✔️ Carrier Chat Exploits & Authorized User Attacks ✔️ IMEI Spoofing, Bribery Chains, & More 🔐 Why SIM Swap Attacks Are Dangerous: - Bypass 2FA codes sent via SMS - Hijack bank, crypto, and email accounts - Control password resets and verification texts - Gain full control of your digital identity 🛡️ How to Protect Yourself from SIM-Swapping in 2025: - Add a SIM lock PIN or carrier port freeze - Remove your phone number from sensitive accounts - Switch to authenticator apps or hardware tokens - Harden your voicemail with a secure PIN - Audit your carrier account for weak links - Never post personal info or your number online 💬 Who Needs to Watch This Video? - Crypto investors - Business professionals - Influencers & high-risk targets - Anyone using SMS for 2FA - Privacy-conscious internet users 🚨 SIM Swap Stats: - Millions lost in crypto SIM-swap thefts annually - 60% of users still rely on SMS for authentication - Carrier support often lacks strong ID verification 👍 Found this helpful? • LIKE the video to beat the algorithm • SUBSCRIBE for weekly cybersecurity tips • COMMENT with your own SIM swap story or question • WATCH the next video: “Every Type of Cyber Attack Explained” for the full playbook 🔗 Useful Tools Mentioned: – Authenticator apps (Google Authenticator, Authy) – SIM lock PINs via your mobile carrier – Have I Been Pwned breach checker – Password managers (Bitwarden, 1Password) – Carrier account freeze options (Verizon, T-Mobile, AT&T) #simswap #simswapping #SIMSwapFraud #cybersecurity #identitytheft #2FA #CryptoSecurity #MobileSecurity #PhoneNumberHijack #VoicemailHack #eSIMExploit #IMEISpoofing #AccountTakeover #PhishingScams #OnlineSafety #CyberCrime #SIMSwapScam #ProtectYourPhone #DigitalSecurity Learn cybersecurity the simple way. Tech in a Teacup serves quick, easy-to-understand videos on cyber attacks, password safety, malware, phishing, and more. Perfect for beginners, non-techies, and anyone who wants to stay safe online—fast.
- 10424Просмотров
- 6 месяцев назадОпубликованоTech in a Teacup
Every SIM-Swap Trick Explained in Detail
Похожее видео
Популярное
томас и его друзья джеймс
Boogeyman vs Stacy Keibler
camp bnos
патерений снайпер фқлм 2
Патеринний снайпер.4серия
Актеры красная гадюка 2025
Потераний снайпер 2
Видео потеряный снайпер
Городскои снаипер 8
the super tall order
Anny_6Feet10
Stevie Emerson
Заставки Тижи TiJi
Игра снайпера 2
Городской снайпер 2
101 далматинец
Красная гадюка3сезон
Потеряний снайпер 2 серія
Барбоскины Лучший день
Bing gets 3 strikes
Потерянный снайпер 4 серия
Бурное безрассудно 2серия
винни пух ну погоди
Красная гадюка 10 серия
Boogeyman vs Stacy Keibler
camp bnos
патерений снайпер фқлм 2
Патеринний снайпер.4серия
Актеры красная гадюка 2025
Потераний снайпер 2
Видео потеряный снайпер
Городскои снаипер 8
the super tall order
Anny_6Feet10
Stevie Emerson
Заставки Тижи TiJi
Игра снайпера 2
Городской снайпер 2
101 далматинец
Красная гадюка3сезон
Потеряний снайпер 2 серія
Барбоскины Лучший день
Bing gets 3 strikes
Потерянный снайпер 4 серия
Бурное безрассудно 2серия
винни пух ну погоди
Красная гадюка 10 серия
Новини