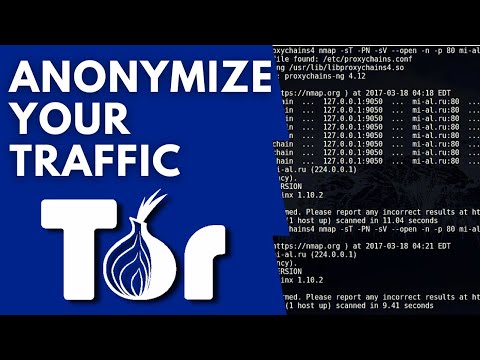
In this in-depth tutorial, we'll delve into the world of Proxychains and Tor, and how they are utilized in Penetration Testing and Cybersecurity. Join us as we stealthily navigate through the covert realms of proxies, Proxychains, VPN's and Tor, exploring their vital roles in penetration testing, OSINT gathering, and web anonymity. You'll discover how to safeguard your digital footprint, overcome geographical restrictions, bypass IDS/IPS systems, and even scan the dark web while harnessing the full potential of Nmap scans with Proxychains and Tor for efficient, silent reconnaissance. This video is part of our ongoing Kali Linux Security Tools series. Don't forget to check out our other content, featuring tutorials on Nmap, Hydra, Metasploit, Nikto, and more, to bolster your cybersecurity expertise. Please Like and Subscribe by clicking here: Follow me on Twitter: Chapters: 00:00 Introduction 01:13 Without a Proxy Explained 03:23 Proxy Servers Explained 04:49 Proxychains Explained 06:23 Tor Explained 08:12 Single Proxy Configuration 14:14 Multi Proxychains Configuration with Nmap scanning demo 18:20 Tor Configuration -- Disclaimer: Hacking without permission is illegal. This channel is strictly for educational purposes only. We cover cybersecurity in the areas of ethical hacking and penetration testing to help make others aware and be better prepared to defend against cyber threats. #tor #proxychains #pentesting #ethicalhacking #kalilinux #kalilinuxsecuritytools #nielsennetworking
- 24903Просмотров
- 2 года назадОпубликованоNielsen Networking
Proxychains and Tor for Penetration Testing: Staying Off the Grid
Похожее видео
Популярное
бен 10
Бобр добр
Стрекоза и муравей
war thunder tech tree
союзмультфильм диск
camp bnos
Городской снаипер 8 серия
6 часть красная гадюка
Universal 2003 hd
история графини де вержи
Красный тарантул 3 часть
гача лайф
Стражи правосудия 3 сезн
Чудо
игра снайпера
bungalow colony
ПОРЧЕННЫЙ
Потеряний снайпер 2
Цена отказа 8 серия
Boo boo song Dana
Лихие 2
Лихач 10-12
Universal effects g major 4
УМ. БЕЛЫЙ ДЕЛЬФИН
Красная годюка
Бобр добр
Стрекоза и муравей
war thunder tech tree
союзмультфильм диск
camp bnos
Городской снаипер 8 серия
6 часть красная гадюка
Universal 2003 hd
история графини де вержи
Красный тарантул 3 часть
гача лайф
Стражи правосудия 3 сезн
Чудо
игра снайпера
bungalow colony
ПОРЧЕННЫЙ
Потеряний снайпер 2
Цена отказа 8 серия
Boo boo song Dana
Лихие 2
Лихач 10-12
Universal effects g major 4
УМ. БЕЛЫЙ ДЕЛЬФИН
Красная годюка
Новини