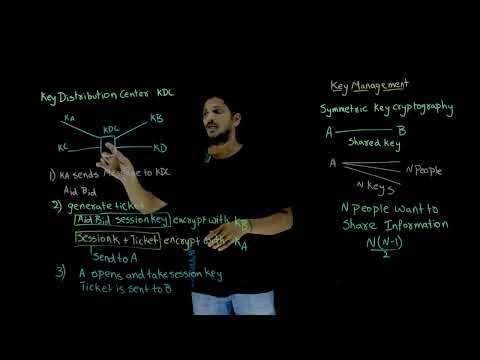
In this lesson, I describe methods of protecting and safely using private and symmetric keys, including secure key generation, separation of duties, dual control, and split knowledge. You can download the script for this video at the beginning or the end of the video.
- 8427Просмотров
- 4 года назадОпубликованоTom Olzak
Cryptography Part 5: Key Management
Похожее видео
Популярное
Preview 2 stars in the sky v7
Dora the explorer
Божественний доктор
سكس
Потерянный снайпер 2 сезон
Грань правосудия 4сезон
forsaken teamers
Universal 1997 2012 1990
Стражи правосудия
Потерянный снайпер 7
Numberblock1 grounded
Universal not scary in Luigi group
Машаимедведь
Sex
Красная гадюка 5
Потеряный снайпер 2 серия
Nickelodeon
Барбоскины Лучший день
Trade scam script
Deep house electro
ПОРЧЕННЫЙ
ШАРЛОТТА ЗЕМЛЯНИКА
КОТ В ШЛЯПЕ
Потеряный снайпер 2
Cartoon network russian
Dora the explorer
Божественний доктор
سكس
Потерянный снайпер 2 сезон
Грань правосудия 4сезон
forsaken teamers
Universal 1997 2012 1990
Стражи правосудия
Потерянный снайпер 7
Numberblock1 grounded
Universal not scary in Luigi group
Машаимедведь
Sex
Красная гадюка 5
Потеряный снайпер 2 серия
Nickelodeon
Барбоскины Лучший день
Trade scam script
Deep house electro
ПОРЧЕННЫЙ
ШАРЛОТТА ЗЕМЛЯНИКА
КОТ В ШЛЯПЕ
Потеряный снайпер 2
Cartoon network russian
Новини