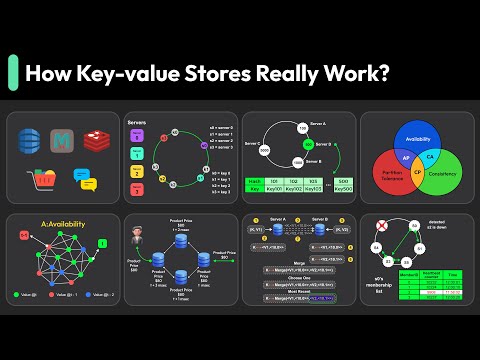
In this episode of Security Blueprint, Abhay Bhargav dissects the security architecture of Redis — one of the most widely used in-memory data stores — through a design and threat modeling lens. From ACLs and protected mode to encryption gaps and data persistence risks, Abhay walks through how Redis’ performance-first design can become a security liability if left unchecked. You’ll learn: 1. Why Redis’ multi-database setup doesn’t actually isolate data 2. How misconfigurations and default exposure lead to compromise 3. Why availability — not just confidentiality — is Redis’ biggest risk 4. How ACLs, namespace isolation, and command restrictions can stop data destruction and exfiltration If Redis sits anywhere in your stack, you’ll want to see how to secure it by architecture, not after a breach. #RedisSecurity #Redis #InMemoryDataStore #CacheSecurity #DatabaseSecurity #securityblueprint #securebydesign #securearchitecture
- 8Просмотров
- 1 неделя назадОпубликованоSecurity Blueprint Society
Redis Security Best Practices | Threat Modeling & Architecture Explained
Похожее видео
Популярное
КРАСНАЯ ГАДЮКА все серии
poland warsaw metro ride from bemowo
красный тарантул часть 3
красная гадюка сезон 2
Wb 2002 effects
Rosie ruined 14 birthday
потерянный снайпер 5
agustin marin i don
Красна я гадюка 6
томас и его друзья елка
Стражи правосудия 3
Умизуми
Лимпопо
dora dasha
Шрек
16 серия красная гадюка
неумолимый 3
mickey Valentine day party part 2
союзмультфильм диск
Лихач 4сезон 10-12
городской снайпер 8 серия
КАТУРИ
Деревяшки
Никелодеон
poland warsaw metro ride from bemowo
красный тарантул часть 3
красная гадюка сезон 2
Wb 2002 effects
Rosie ruined 14 birthday
потерянный снайпер 5
agustin marin i don
Красна я гадюка 6
томас и его друзья елка
Стражи правосудия 3
Умизуми
Лимпопо
dora dasha
Шрек
16 серия красная гадюка
неумолимый 3
mickey Valentine day party part 2
союзмультфильм диск
Лихач 4сезон 10-12
городской снайпер 8 серия
КАТУРИ
Деревяшки
Никелодеон
Новини