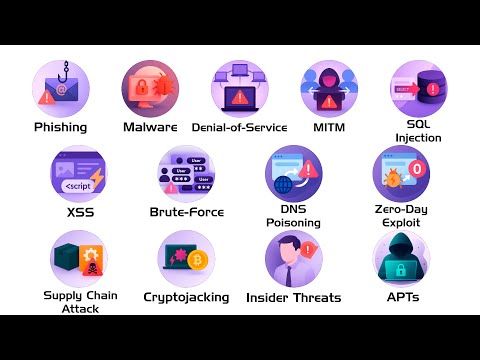
Every Computer virus Explained in 7 Minutes From classic viruses and worms to advanced threats like zero-day exploits and fileless malware, this video breaks down the most common (and dangerous) forms of malware you need to know about. 👉 Learn what each threat does, how it spreads, and how to protect yourself. Perfect for students, tech enthusiasts, and anyone curious about cybersecurity. 🦠 Covered in this video: Malware, Viruses & Worms Trojan Horses & Ransomware Spyware, Adware & Rootkits Keyloggers & Botnets Zero-Day Exploits & Phishing Social Engineering & Drive-by Downloads Logic Bombs, Fileless Malware & Backdoors Exploit Kits & Scareware ⚠️ Stay safe online by keeping your software updated, avoiding suspicious links, and learning how hackers use these techniques. If you found this helpful, don’t forget to 👍 like, 💬 comment, and 🔔 subscribe for more cybersecurity breakdowns! #ComputerViruses #Malware #CyberSecurity #TrojanHorse #Ransomware #Spyware #Adware #Rootkit #Keylogger #Botnet #ZeroDay #Phishing #SocialEngineering #DriveByDownload #LogicBomb #FilelessMalware #Backdoor #ExploitKits #Scareware #Worms #VirusExplained #TechEducation #InfoSec #Hacking What are computer viruses Types of computer malware explained How do Trojans and ransomware work Difference between spyware and adware Rootkits and keyloggers explained Botnets and how hackers control computers Zero day exploit tutorial Phishing scams explained Social engineering in cybersecurity Drive by download malware Logic bomb virus explained Fileless malware example Backdoor in hacking Exploit kits in cybersecurity Scareware virus explained Computer worms vs viruses How to protect your PC from malware Cybersecurity for beginners Internet safety tips 2025
- 3213Просмотров
- 2 месяца назадОпубликованоinformation discovery
Every Computer virus Explained in 7 Minutes
Похожее видео
Популярное
Картоплини та дракони
Красная гадюка 4серия
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
ну погоди 1-16 выпуски
макс и катя новогодний
Preview 2 stars in the sky v38
little girls naked
encounter fnf ai
Illumination 2024
Актеры красная гадюка 2025
ШПИОН И ШЛЯПЫ КОРОЛЕВЫ
Потерянный снайпер 1 серия
Жена чиновника 3 часть
ВЕЛОСПОРТ ЮРИЙ ПЕТРОВ .
ДАША ПУТЕШЕСТВЕННИЦА
40 или Геометрия любви
Безжалостный гений часть5
Alizeh agnihotri
випуск
Красная гадюка 23 серия
тупи и бину
РЫЦАРЬ МАЙК
Поточний снайпер 2 часть
Красная гадюка 12 серія
Красная гадюка 4серия
ПОТЕРЯННЫЙ СНАЙПЕР 2 серия
ну погоди 1-16 выпуски
макс и катя новогодний
Preview 2 stars in the sky v38
little girls naked
encounter fnf ai
Illumination 2024
Актеры красная гадюка 2025
ШПИОН И ШЛЯПЫ КОРОЛЕВЫ
Потерянный снайпер 1 серия
Жена чиновника 3 часть
ВЕЛОСПОРТ ЮРИЙ ПЕТРОВ .
ДАША ПУТЕШЕСТВЕННИЦА
40 или Геометрия любви
Безжалостный гений часть5
Alizeh agnihotri
випуск
Красная гадюка 23 серия
тупи и бину
РЫЦАРЬ МАЙК
Поточний снайпер 2 часть
Красная гадюка 12 серія
Новини