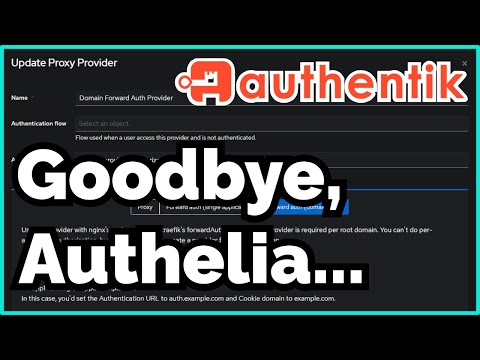
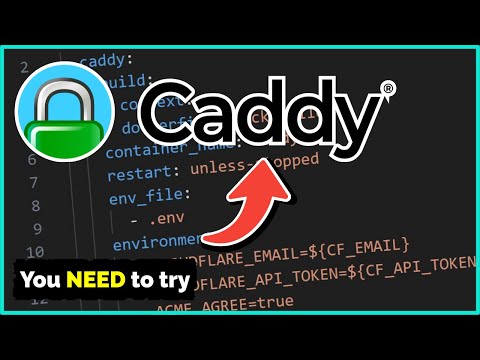
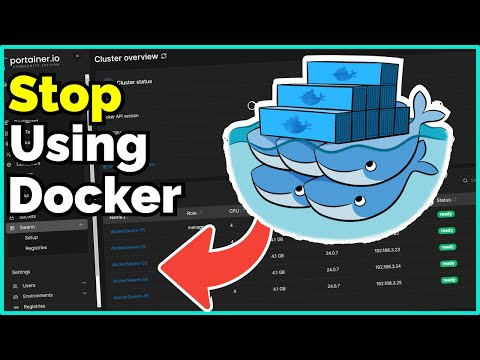
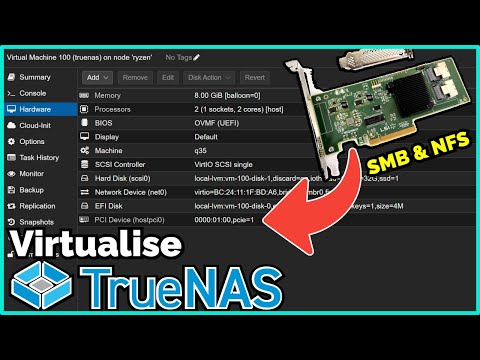
The majority of Traefik tutorials all have the same problem, they expose all services routed through Traefik to the Internet. This is bad from a security perspective and increases the attack surface for your homelab. It's not a good idea to externalise Portainer, PiHole, Vaultwarden etc... In this video I provide 3 options to restrict access to applications so you can specify exactly which services you want to expose and to which clients. Let's secure Traefik now! Traefik Docker Files: Recommended Hardware: 's-Guide/ Discord: Twitter: Reddit: GitHub: 00:00 - Introduction to the Traefik 'Security Problem' 01:29 - Demonstrating the 'Problem' 03:23 - Option 1: Cloudflare Proxy 05:00 - Option 2: Multiple Traefik Entrypoints 14:44 - Option 3: Traefik WhiteList 19:20 - Bonus Option: Deploy Two Traefik Instances 20:30 - Outro
- 120385Просмотров
- 2 года назадОпубликованоJim's Garage
DONT Expose Internal Applications To The Internet! Restrict Access NOW!
Похожее видео
Популярное
mickey mouse clubhouse
Краснаямгадюка 2 сезон
efootball
САЛЛИ БОЛЛИВУД
дисней добрлас
trotro
klaskyklaskyklaskyklasky remastered joey 2 do go
обнаженная
Rosie Misbehaves on the trip to Tokyo
Лихач 7-9
карусель
Дорама вечная любовь
Бит и его
Смешари
майя сказочница
健屋
Chloe birthday
Пим и пэм
Teletubbies
grasshopper code
смешарики чиполлино
женитьба бальзаминова
Красная гадюка 6 серия
Краснаямгадюка 2 сезон
efootball
САЛЛИ БОЛЛИВУД
дисней добрлас
trotro
klaskyklaskyklaskyklasky remastered joey 2 do go
обнаженная
Rosie Misbehaves on the trip to Tokyo
Лихач 7-9
карусель
Дорама вечная любовь
Бит и его
Смешари
майя сказочница
健屋
Chloe birthday
Пим и пэм
Teletubbies
grasshopper code
смешарики чиполлино
женитьба бальзаминова
Красная гадюка 6 серия
Новини