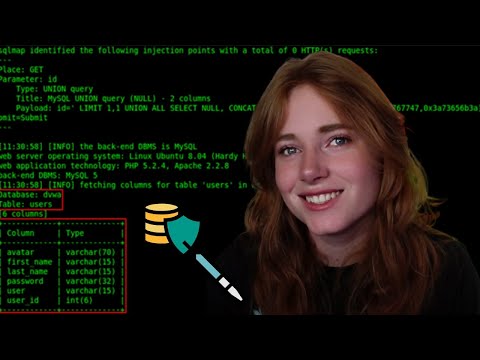
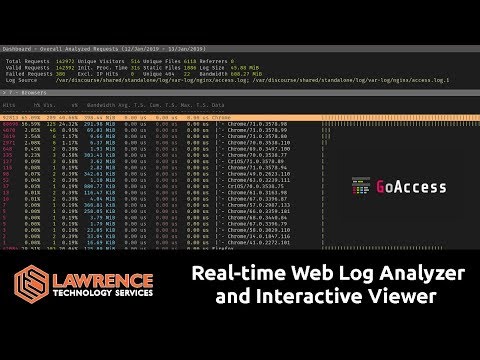
Welcome to Log Analysis 101 🔍 — Episode 1: Web Log Analysis Made Simple If you’ve ever opened a log file and thought, “What is this alien language?!” — you’re not alone. In this series, I’ll guide you step by step on how to understand, analyze, and use logs like a true SOC analyst. In this episode, you’ll learn: ✅ What web server logs are and why they matter ✅ Types of logs (Access Logs & Error Logs) ✅ Real-world log examples explained line by line ✅ How attackers leave their footprints in logs ✅ Why logs are critical for cybersecurity & incident response By the end of this video, you’ll see logs not as random gibberish — but as stories. Stories that reveal who visited your site, who tried to hack it, and what really happened on your server. This is the first video in my Log Analysis Series, where we’ll cover: 🔹Web server logs 🔹Authentication logs 🔹System logs 🔹Threat hunting in logs 🔹Real-world SOC investigations 🌐 Timestamps: 00:00 – Intro: Why Log Analysis? 01:22 – What Are Web Server Logs? 01:58 – Types of Logs: Access & Error Logs 05:15 – Access Log Examples Explained 07:40 – Error Log Examples Explained 09:24 – Why Logs Matter in Cybersecurity 09:52 – Wrap-up & Next Episode Teaser 🎓 If you’re starting your SOC analyst journey, this series is for you! 👉 Don’t forget to Subscribe and hit the 🔔 to follow along as we decode the world of logs together! #LogAnalysis #Cybersecurity #SOCanalyst #IncidentResponse #WebServerLogs #AccessLogs #ErrorLogs #SIEM #BlueTeam #CyberSecurityForBeginners #InfosecPandey
- 209Просмотров
- 3 месяца назадОпубликованоInfoSec Pandey