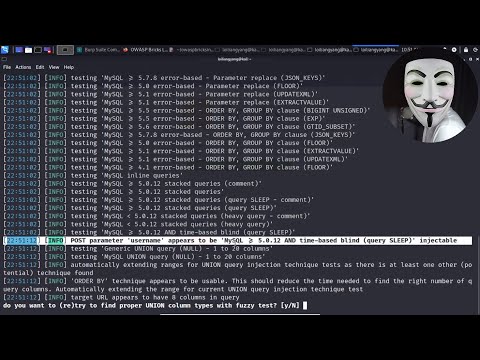
A single mistake in website development can lead to full compromise via SQL injection. Here’s how, safely explained. This video is for educational and awareness purposes only. It was performed in a safe, controlled lab environment to raise awareness about common web security flaws like SQL injection. The goal is to help developers and cybersecurity practitioners understand how these attacks work and how to prevent them. ▬▬ Tools Used ▬▬ - Kali Linux: attacker machine - Apache + PHP + MySQL: vulnerable website - Python: generate username wordlists - Hydra: brute-force username enumeration - SQL Scripting: SQL injection ▬▬ ⏱️ Chapters ▬▬ 00:00 Prologue 00:58 Setup & Database 02:27 Build Username List with Python 06:13 Username Enumeration 09:09 Understanding SQL Injection 10:58 SQL Injection: Gaining Admin Access 11:59 How to protect #penetrationtesting #sqlinjection #cybersecurity Join Ethical Hacker Diaries to get access to perks: @UCUOlY1VUTHMdkLph5ORHF2Q
- 245411Просмотров
- 2 месяца назадОпубликованоEthical Hacker Diaries
How Hackers Use SQL Injection to Get Into Websites
Похожее видео
Популярное
Molest
Грань правосудия 1 серия
Баскервиллей
РЫЦАРЬ МАЙК
Tantric awakening shaft
Фильм потерянный снайпер
врумиз реклама
Грань правосудия фильм 4
Бит и его
Грань правосудия 4сезон
Актеры красной гадюки
малыш вилли 03
Rosie ruined 14 birthday
пупок женщины
союзмультфильм
Фивел
лалалупси шоколад
Потеряный снайпер 5 серия
Потерянный снайпер 4 серия
women relax at pool
Потеряный снайпер 1
Красная гадюка 16 серия
Потерянный снайпер 9 серия
6серия
Лихач 3 сезон 10-12
Грань правосудия 1 серия
Баскервиллей
РЫЦАРЬ МАЙК
Tantric awakening shaft
Фильм потерянный снайпер
врумиз реклама
Грань правосудия фильм 4
Бит и его
Грань правосудия 4сезон
Актеры красной гадюки
малыш вилли 03
Rosie ruined 14 birthday
пупок женщины
союзмультфильм
Фивел
лалалупси шоколад
Потеряный снайпер 5 серия
Потерянный снайпер 4 серия
women relax at pool
Потеряный снайпер 1
Красная гадюка 16 серия
Потерянный снайпер 9 серия
6серия
Лихач 3 сезон 10-12
Новини