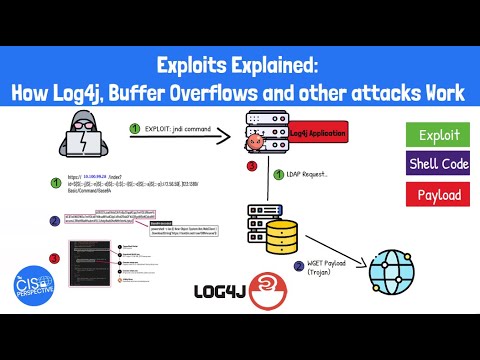
Bypassing multi-factor authentication was once considered more of a proof of concept then an actual threat. In this video, we will review four common techniques an attacker will utilize to hack multi-factor and two-factor authentication. We’ll review Evilgenix2, which is a popular framework for stealing authentication cookies, and other methods that an attacker can utilize to bypass the authentication process. 1:06 Evilgenix2 Framework 2:51 Evilgenix Defense and Protection 3:45 Pass the Cookie 5:10 Pass the Cookie Defense and Protection 5:56 SMS Man-in-the-Middle 6:34 SIM Swap 8:13 Attack on Soft and Hard Tokens 9:22 Hard Token Example Resources/Links -Evilgenix GitHub: -Pass the Cookie example: -Android 0-day SMS: 👇 More Info 👇 Animations by TCP Media: Viral content. Tech-first thinking. White-glove service. 🎯 Need content like this? Visit for high-impact technical marketing.
- 78850Просмотров
- 3 года назадОпубликованоThe CISO Perspective
Hacking Two Factor Authentication: Four Methods for Bypassing 2FA and MFA
Похожее видео
Популярное
RafałBrzozowski
Игра снайпера 2
ultramen
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
Красная гадюка все серии
forsaken teamers
Красная гадюка 2
Nickelodeon
тарзан фильм
Красная гадюка часть 3
Mesis purple
Красная гадюка 11 серия
Preview Disney 2011 effects
Финал
Spongebob
Molest
сильвания фэмили реклама
ГАЗОН В ПУТИ ПОСЛЕДНИЕ
Fap teen
Малыш хиппо
Деревяшки
Темное наследие
детский сад
timon pumbaa
губка боб ловкий кран
Игра снайпера 2
ultramen
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
Красная гадюка все серии
forsaken teamers
Красная гадюка 2
Nickelodeon
тарзан фильм
Красная гадюка часть 3
Mesis purple
Красная гадюка 11 серия
Preview Disney 2011 effects
Финал
Spongebob
Molest
сильвания фэмили реклама
ГАЗОН В ПУТИ ПОСЛЕДНИЕ
Fap teen
Малыш хиппо
Деревяшки
Темное наследие
детский сад
timon pumbaa
губка боб ловкий кран
Новини