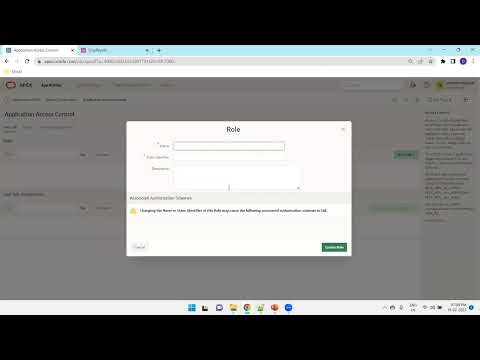
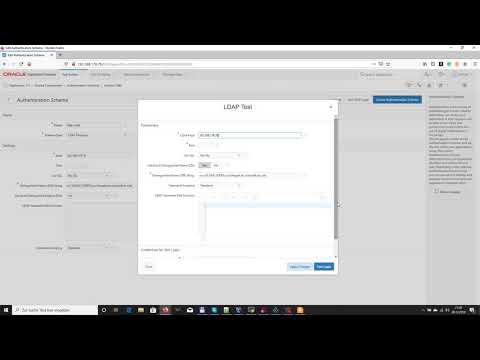
Oracle APEX Authorization Schemes | Security Features Explained In this video, I provide a detailed explanation of the security features in Oracle APEX authorization schemes, which allow developers to control user access at various levels, including menus, pages, buttons, and individual items. Proper authorization ensures that only the right users have access to specific components of an application, enhancing both security and user experience. One of the most effective ways to implement role-based access control in Oracle APEX is through the Access Control List (ACL). By defining permissions and roles, you can dynamically show or hide different elements within your application based on user privileges. This approach helps safeguard sensitive information and prevents unauthorized actions. Whether you're building an enterprise-grade application or a small-scale project, understanding authorization schemes is crucial for maintaining a secure and well-structured Oracle APEX environment. Topics Covered in This Video: What are Oracle APEX Authorization Schemes? Learn the fundamentals of authorization in Oracle APEX and how it differs from authentication. How to Restrict Access to Pages, Buttons, and Menu Items Understand how to define and apply security rules to control user interactions within the app. Implementing ACL (Access Control List) in APEX Step-by-step guide on creating and managing an Access Control List to define user roles and permissions. Best Practices for Securing Your Oracle APEX Applications Tips and strategies to enhance security and prevent unauthorized access to sensitive data. Oracle APEX security, APEX authorization schemes, Access Control List in Oracle APEX, role-based access control in APEX, APEX authentication vs authorization, Oracle APEX access management, hide and show elements in APEX, secure Oracle APEX applications
- 2133Просмотров
- 10 месяцев назадОпубликованоERPstuff
Oracle APEX Authorization Schemes | Security Features Explained
Похожее видео
Популярное
poland warsaw metro ride from bemowo
Universal weird code
xxxxxx
eiprill
Etta Mae Hartwell
2.0 I killed universal
потерянній снайпер
the 70s show
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
Плюсплюс
Потерянный снайпер 2 сезон
губка боб ловкий кран
Фивел
Фильм грань правосудия 2
Universal 2010 g major effects
Красная гадюка 5 серия
poterianij snaiper 2 seria
Коля оля и архимед
Финал
Dora the explorer
СТРАЖИ ПРАВОСУДИЯ 4
массаж поджелудочной
ГАЗОН В ПУТИ ПОСЛЕДНИЕ
Поточний снайпер 2 часть
Universal weird code
xxxxxx
eiprill
Etta Mae Hartwell
2.0 I killed universal
потерянній снайпер
the 70s show
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
Плюсплюс
Потерянный снайпер 2 сезон
губка боб ловкий кран
Фивел
Фильм грань правосудия 2
Universal 2010 g major effects
Красная гадюка 5 серия
poterianij snaiper 2 seria
Коля оля и архимед
Финал
Dora the explorer
СТРАЖИ ПРАВОСУДИЯ 4
массаж поджелудочной
ГАЗОН В ПУТИ ПОСЛЕДНИЕ
Поточний снайпер 2 часть
Новини