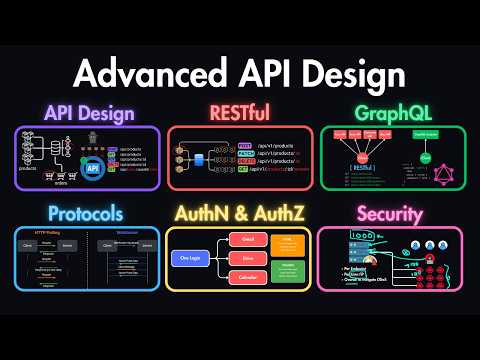
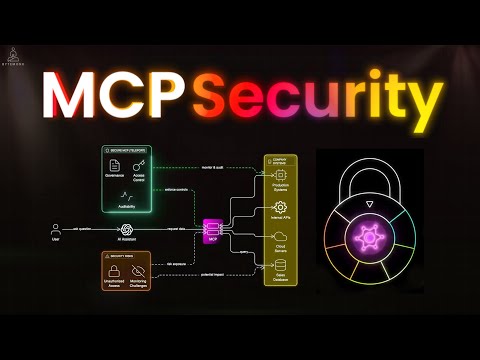
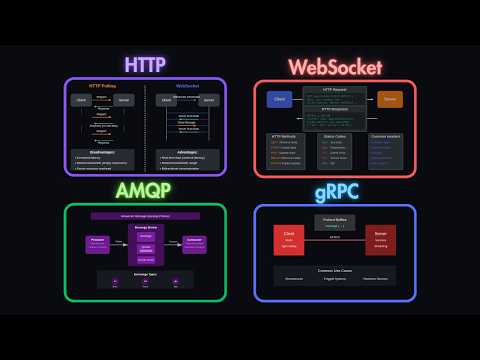
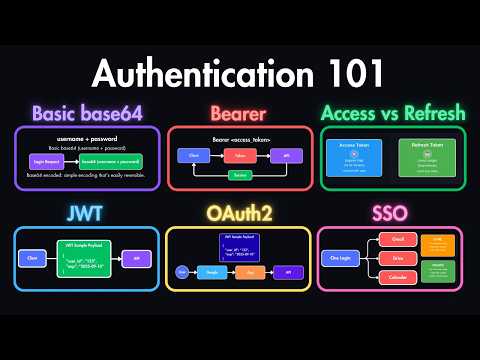
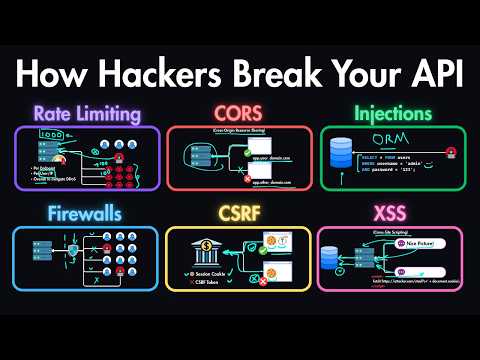
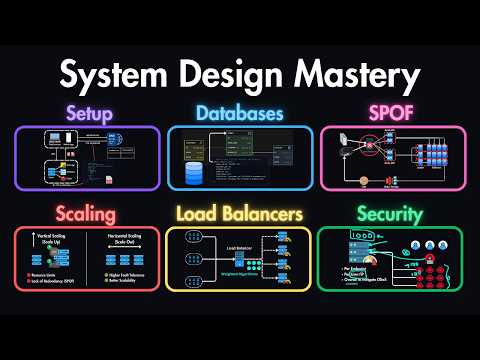
Become a Remote Senior Software Engineer with a Job Guarantee: Learn how real-world systems control what users can do using authorization models like RBAC, ABAC, and ACL. 🔖 Sections 0:00 Introduction 0:52 What is Authorization 1:47 Authorization Models 2:54 RBAC: Role-Based Access Control 3:58 ABAC: Attribute-Based Access Control 5:31 ACL: Access Control Lists 7:26 Delegated Authorization with OAuth2 9:12 Token-Based Authorization 10:19 Recap
- 30897Просмотров
- 4 месяца назадОпубликованоHayk Simonyan
Authorization Explained: When to Use RBAC, ABAC, ACL & More
Похожее видео
Популярное
КРАСНАЯ ГАДЮКА 15серия
Dora FULL EPISODES Marathon!
Потерянный снайпер часть 2
barefoot jewish women
Сезон охоты
Потеряний снайпер 2
Красная гадюка 2
красный тарантул часть 3
poterianij snaiper 3 seria
чаггингтон
4 серия
undefined
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
карусель
Поточний снайпер 2
маленький шеф карусель
Valu stupid wife temporada finale series
Bing but it’s ruined in sora 2
союзмультфильм
Безжалостный гений часть5
لخت
Alizeh agnihotri
Красная гадюка 6 серия
Dora FULL EPISODES Marathon!
Потерянный снайпер часть 2
barefoot jewish women
Сезон охоты
Потеряний снайпер 2
Красная гадюка 2
красный тарантул часть 3
poterianij snaiper 3 seria
чаггингтон
4 серия
undefined
ПОТЕРЯННЫЙ СНАЙПЕР 5 сери
карусель
Поточний снайпер 2
маленький шеф карусель
Valu stupid wife temporada finale series
Bing but it’s ruined in sora 2
союзмультфильм
Безжалостный гений часть5
لخت
Alizeh agnihotri
Красная гадюка 6 серия
Новини