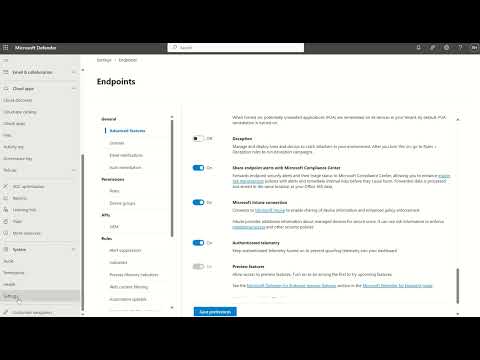
🔐 Learn How to Configure Email & Collaboration Settings in Microsoft Defender for Office 365 | Step-by-Step Guide 🛡️ In this video, we walk you through how to configure the Email & Collaboration settings in Microsoft Defender for Office 365 to enhance your organization's security posture. These settings help protect your users from phishing, malware, spoofing, and other advanced threats targeting email and collaboration tools like SharePoint, Teams, and OneDrive. 📌 What You'll Learn: Overview of Defender for Office 365 features Navigating to the Microsoft 365 Security & Compliance Center Configuring anti-phishing, anti-malware, and anti-spam policies Setting up safe links and safe attachments Best practices for collaboration security across Teams, SharePoint, and OneDrive Reporting, monitoring, and alerting setup 🧠 Who Should Watch: IT admins, Microsoft 365 Security Engineers, Cloud Architects, and anyone managing Microsoft 365 environments. 👉 Don’t forget to like, share, and subscribe for more M365 and security configuration videos! #Microsoft365 #DefenderForOffice365 #EmailSecurity #MicrosoftDefender #Office365Security #CyberSecurity #CloudSecurity #Microsoft365Admin ================================================= WHO AM I? If we haven’t met before - Hey 👋 I’m Vinod, an IT Professional loves to learn, teach and explore more about the Microsoft 365, Microsoft Azure and FinOps and overall other cloud computing topics and Through my videos here on this channel, I share evidence-based topics and strategies and tools to help you be more productive, learn and be expert and build something you love spending time a life you love. ================================================== Connect with Vinod Survase on Social Media # =============== Disclaimer: The information provided in this video is for educational and informational purposes only. While we strive to ensure the accuracy and relevance of the information shared, it should not be taken as professional or official advice. The views expressed in this video are personal opinions and do not necessarily reflect those of my employer or any affiliated entities. Please note that some topics discussed may involve specific software, tools, or platforms. Always consult the official documentation, seek professional assistance, or consult your organization’s policies before implementing any suggestions from this video. I am not responsible for any loss, damage, or inconvenience caused as a result of the information presented. Use the content in this video at your own discretion and verify any actions before applying them in your environment.
- 502Просмотров
- 5 месяцев назадОпубликованоThe Azure 365 Hub
How to Configure Email & Collaboration setting in Defender for Office 365
Похожее видео
Популярное
Красная гадюка 17-20 серии
Чудо
топтыжка
Hey Arnold temporada 1 capitulo 20
Лихач 3 сезон 1-4
КРАСНАЯ ГАДЮКА 13 serija
Потерянный снайпер 6серия
кошечки собачки
чиполлино
взлом карусели
klaskyklaskyklaskyklasky gummy bear g major 26
reupload my edited video bb into song version
Preview 2 stars in the sky v38
мальчики
ЛЯПИК ЕДЕТ В ОКИДО
макс и катя
Красная гадюка часть 3
forsaken fandom
Никелодеон реклама
2х2 лёлик и барбарики
dominant
Грань провосудия 4серия
Mufasa the lion king shaju
Красная гадюка 16 серия
Чудо
топтыжка
Hey Arnold temporada 1 capitulo 20
Лихач 3 сезон 1-4
КРАСНАЯ ГАДЮКА 13 serija
Потерянный снайпер 6серия
кошечки собачки
чиполлино
взлом карусели
klaskyklaskyklaskyklasky gummy bear g major 26
reupload my edited video bb into song version
Preview 2 stars in the sky v38
мальчики
ЛЯПИК ЕДЕТ В ОКИДО
макс и катя
Красная гадюка часть 3
forsaken fandom
Никелодеон реклама
2х2 лёлик и барбарики
dominant
Грань провосудия 4серия
Mufasa the lion king shaju
Красная гадюка 16 серия
Новини