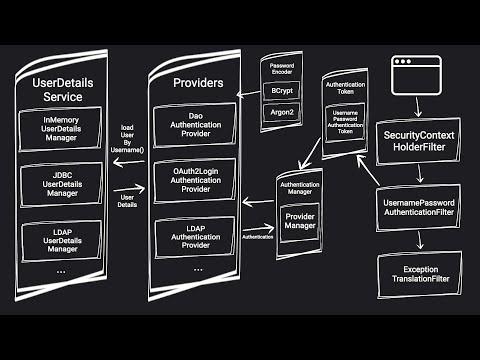
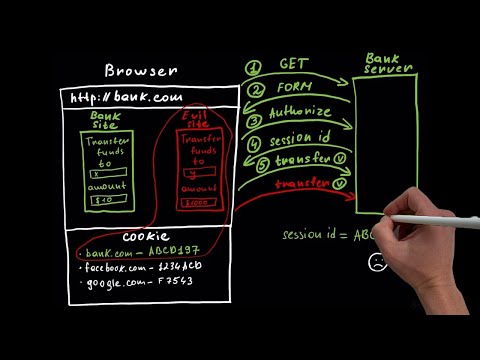
In this YouTube video, we're going to put a "hacker" hoodie and demonstrates a CSRF attack on a fake banking website to show how it works. Disclaimer - hacking or penetration testing without prior authorization is illegal. We're going to look how to protect against CSRF attacks using two methods from Spring Security: the SameSite Attribute and the Synchronizer Token Pattern. The SameSite Attribute can prevent the browser from sending cookies for cross-site requests, while the CSRF token is a random string that the server generates and returns to the client to ensure that the request is coming from a legitimate source. Github Repo - Docker command - docker run -p 8080:8080 -t skryvets/csrf-vulnerable-spring-application Spring official documentation regarding CSRF - 👋🏻Connect with me: Website: Twitter: Github: LinkedIn: SUBSCRIBE TO MY CHANNEL: @sergey_tech?sub_confirmation=1 ❤️ Chapters 0:00 Introduction 0:28 Disclaimer 0:42 Project Intro 1:17 Project Overview 2:44 Creating the Exploit 3:27 Implementing the Solution 7:32 Solution Deep Dive: What Happened 8:31 Preventing CSRF Attacks: Overview 8:59 SameSite Attribute: Explained 12:53 CSRF Token: Explained 15:34 Types of Malicious Browsers and How Scammers Trick Users 16:39 Conclusion
- 5065Просмотров
- 2 года назадОпубликованоSergey Tech
Dangers of CSRF Attacks and How to Prevent Them in Spring Boot App
Похожее видео
Популярное
Nude yoga
Halloween boo boo s
Molest
Семья от а до Я
mia malkova hot tub
forsaken teamers
РЫЦАРЬ МАЙК
Preview 2 stars in the sky v38
Красный тарантул 3
Dia de piscina com as meninas
Даша
Красная гадюка 13серия
ZERO FORTY FIVE
Дельфин 3
xxxxxx
Потериани снаипер 3 серя
Wb not scary
врумиз реклама
Потерянный снайпер 3 серия
Волшебная карусель
потеряный снайпер 3 серия
Поточний снайпер 2 часть
потеренный снайпер 2
Безжалостный гений 3
Halloween boo boo s
Molest
Семья от а до Я
mia malkova hot tub
forsaken teamers
РЫЦАРЬ МАЙК
Preview 2 stars in the sky v38
Красный тарантул 3
Dia de piscina com as meninas
Даша
Красная гадюка 13серия
ZERO FORTY FIVE
Дельфин 3
xxxxxx
Потериани снаипер 3 серя
Wb not scary
врумиз реклама
Потерянный снайпер 3 серия
Волшебная карусель
потеряный снайпер 3 серия
Поточний снайпер 2 часть
потеренный снайпер 2
Безжалостный гений 3
Новини