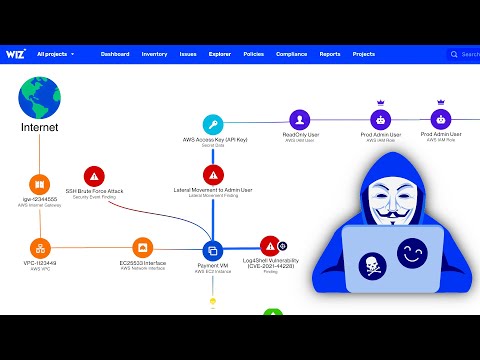
In this episode, Kody and Killian go over more advanced methods of exploiting Windows systems, and how to escalate privileges beyond the initial compromised devices. Sign up for our e-mail alerts to stay updated when we go live & register to win free swag: Chapters: 0:00 Countdown 9:57 Intro 12:04 Phishing Email 14:40 Reverse Shell 18:35 Network Enumeration 21:33 Lateral Movement 24:14 Finding Interesting Data 29:08 DNS Tunneling 33:19 Closing Thoughts 41:19 End Screen
- 882Просмотров
- 5 лет назадОпубликованоSecurityFWD
Exploiting Windows & Privilege Escalation
Похожее видео
Популярное
привет я николя все серии
Гранд правосудия 4
союзмультфильм
ЖИЗНЬ ПЕТРОВИЧА В США
4 серия
комедия
Поточний снайпер 2 часть
Патеринний снайпер.4серия
przepraszamy za usterki
Bing German
Красная кадыка 2
энчантималс реклама
Грань правосудия 5
Грань правосудия 4сезон
микки на фабрике смеха
телеканал детский
Universal g major 7
Потерянный снайпер 6
томас и его друзья елка
Обризи
Dino Dan where the dinosaurs are
Городской снайпер 1 серия
Красная гадюка 5часть
клуб микки мауса
потерянный сгайпер
Гранд правосудия 4
союзмультфильм
ЖИЗНЬ ПЕТРОВИЧА В США
4 серия
комедия
Поточний снайпер 2 часть
Патеринний снайпер.4серия
przepraszamy za usterki
Bing German
Красная кадыка 2
энчантималс реклама
Грань правосудия 5
Грань правосудия 4сезон
микки на фабрике смеха
телеканал детский
Universal g major 7
Потерянный снайпер 6
томас и его друзья елка
Обризи
Dino Dan where the dinosaurs are
Городской снайпер 1 серия
Красная гадюка 5часть
клуб микки мауса
потерянный сгайпер
Новини