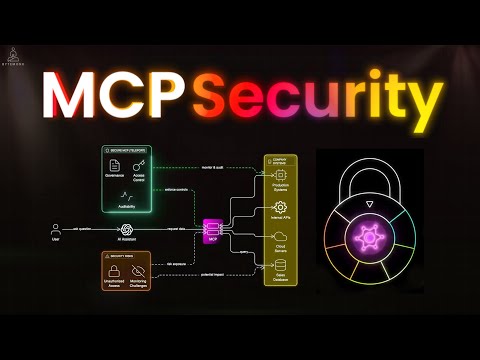
Supabase just changed the game with MCP ( Model Context Protocol). With rise of vibe coding tools like Lovable that rely on SupaBase as Backend As Service Platform of choice , developer adoption is also on the rise. But vibe coding without proper guard rails is dangerous. In this video we go over a case study of one such scenario where AI Agent can be tricked via Prompt Injection to leak and entire SQL Database. Topics: • What is Model Context Protocol and how it lets LLMs access your project context. • Why “Defense in Depth” suddenly matters more than ever for Supabase developers. • How a single misconfiguration could expose your entire SQL database to an AI model. • How prompt injection, unsafe permissions, and unguarded MCP endpoints can increase vulnerability Chapters: 00:00 - Intro 00:38 - vibecoding setup 01:44 - The attack explained 02:33 - what went wrong ? 02:55 - Key ingredients needed for attack 03:26 - how to stay safe ? 04:05 - Conclusion 📚 Sources: • Supabase — Defense in Depth for MCP Servers: • GeneralAnalysis — Supabase MCP can leak your entire SQL database: Attribution: Mechanolith by Kevin MacLeod is licensed under a Creative Commons Attribution 4.0 license. Source: Artist: #supabase #buildwithai #promptinjection
- 197Просмотров
- 1 месяц назадОпубликованоLet The Devs Cook
Dont trust your AI Agents. Cursor & Supabase MCP.
Похожее видео
Популярное
Chorded universal 2010
томас и его друзья песня
дорожная азбука
poterianij snaiper 4 seria
крот и автомобильчик
harry sisson trump
Dia de piscina com as meninas
formation
Смешари Пин код
ШАРЛОТТА ЗЕМЛЯНИКА
Поточний снайпер 2
чужой район 2 сезон
Безжалостный гений 3
Preview 2 stars in the sky v4
Halloween boo boo s
reupload my edited video bb into song version
Tel ali
майя сказочница
Дорама вечная любовь
Потерянный спайпер 2
ПЕРСИ И ЕГО ДРУЗЬЯ
blaze monster machines
барбоскины обзор диск
Потерянный снайпер 1 серия
томас и его друзья песня
дорожная азбука
poterianij snaiper 4 seria
крот и автомобильчик
harry sisson trump
Dia de piscina com as meninas
formation
Смешари Пин код
ШАРЛОТТА ЗЕМЛЯНИКА
Поточний снайпер 2
чужой район 2 сезон
Безжалостный гений 3
Preview 2 stars in the sky v4
Halloween boo boo s
reupload my edited video bb into song version
Tel ali
майя сказочница
Дорама вечная любовь
Потерянный спайпер 2
ПЕРСИ И ЕГО ДРУЗЬЯ
blaze monster machines
барбоскины обзор диск
Потерянный снайпер 1 серия
Новини